Smart Routing et HTTPS pour tous
Traefik en action !


How to use these slides?
Browse the slides: Use the arrows
Change chapter: Left/Right arrows
Next or previous slide: Top and bottom arrows
Overview of the slides: keyboard’s shortcut "o"
Speaker mode (and notes): keyboard’s shortcut "s"
Whoami
Damien DUPORTAL:
Træfik's Developer 🥑 Advocate @ Containous

Containous
We Believe in Open Source
We Deliver Traefik
Commercial Support for Traefik
20 people, 90% tech

Why Traefik?

Why, Mr Anderson?
Evolution of Software Design
The Premise of Microservices…

…and What Happens

Tools of the Trade













Where’s My Service?
What If I Told You?

That You Don’t Have to Write This Configuration File…?
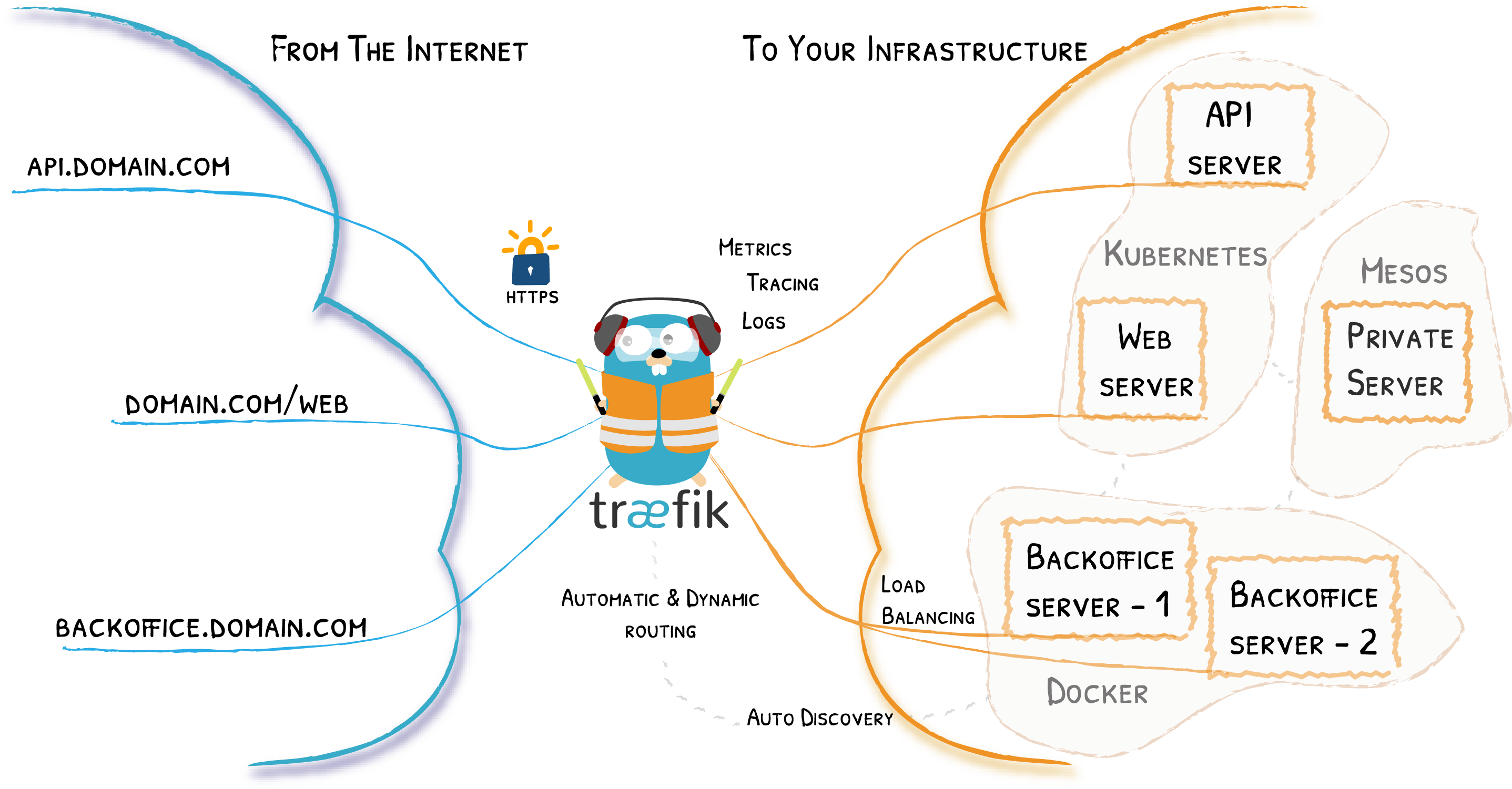
Here Comes Traefik!
Traefik Project
MIT License
Written in Go
21,000+ ⭐
600M+ ⬇️
350+ 👷
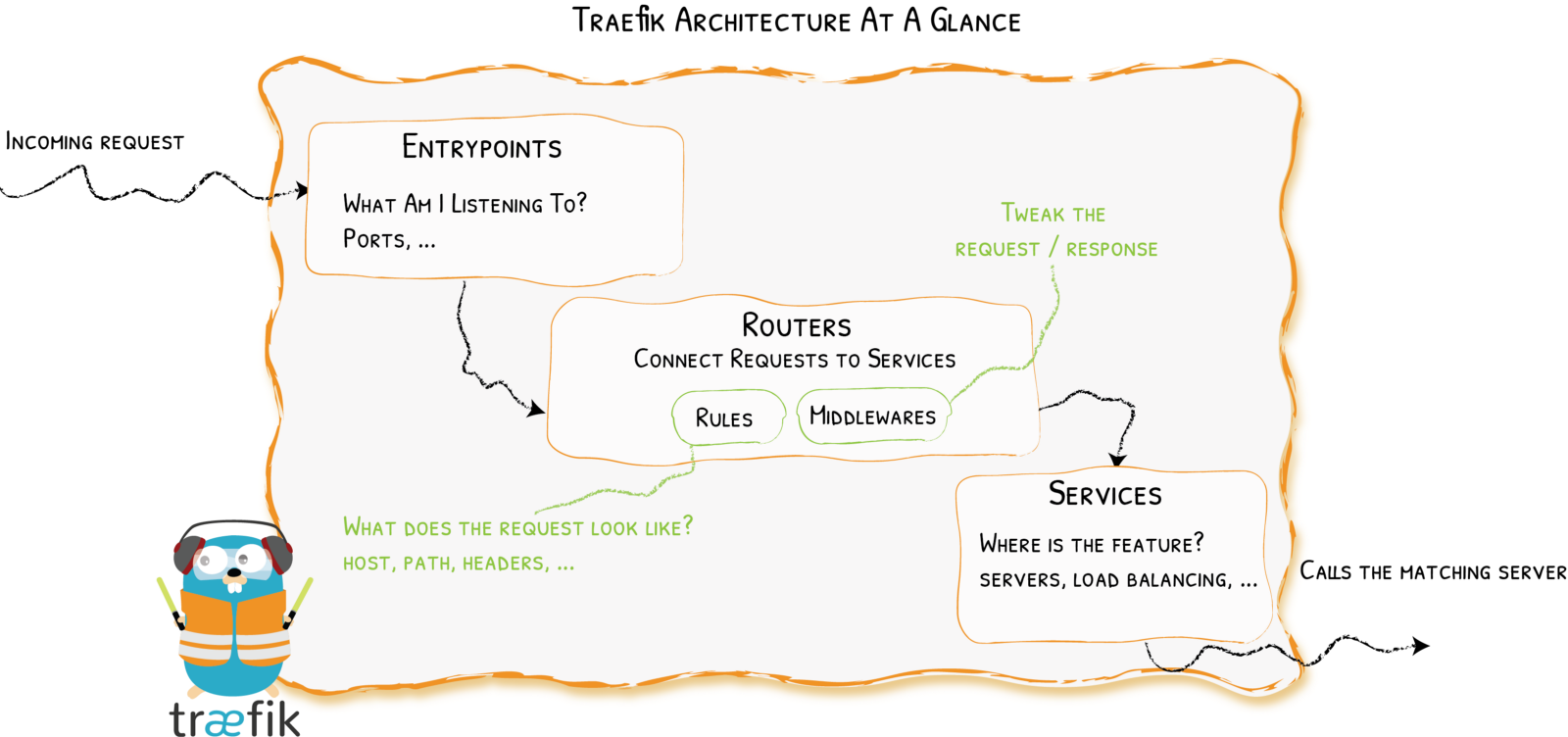
Traefik Core Concepts

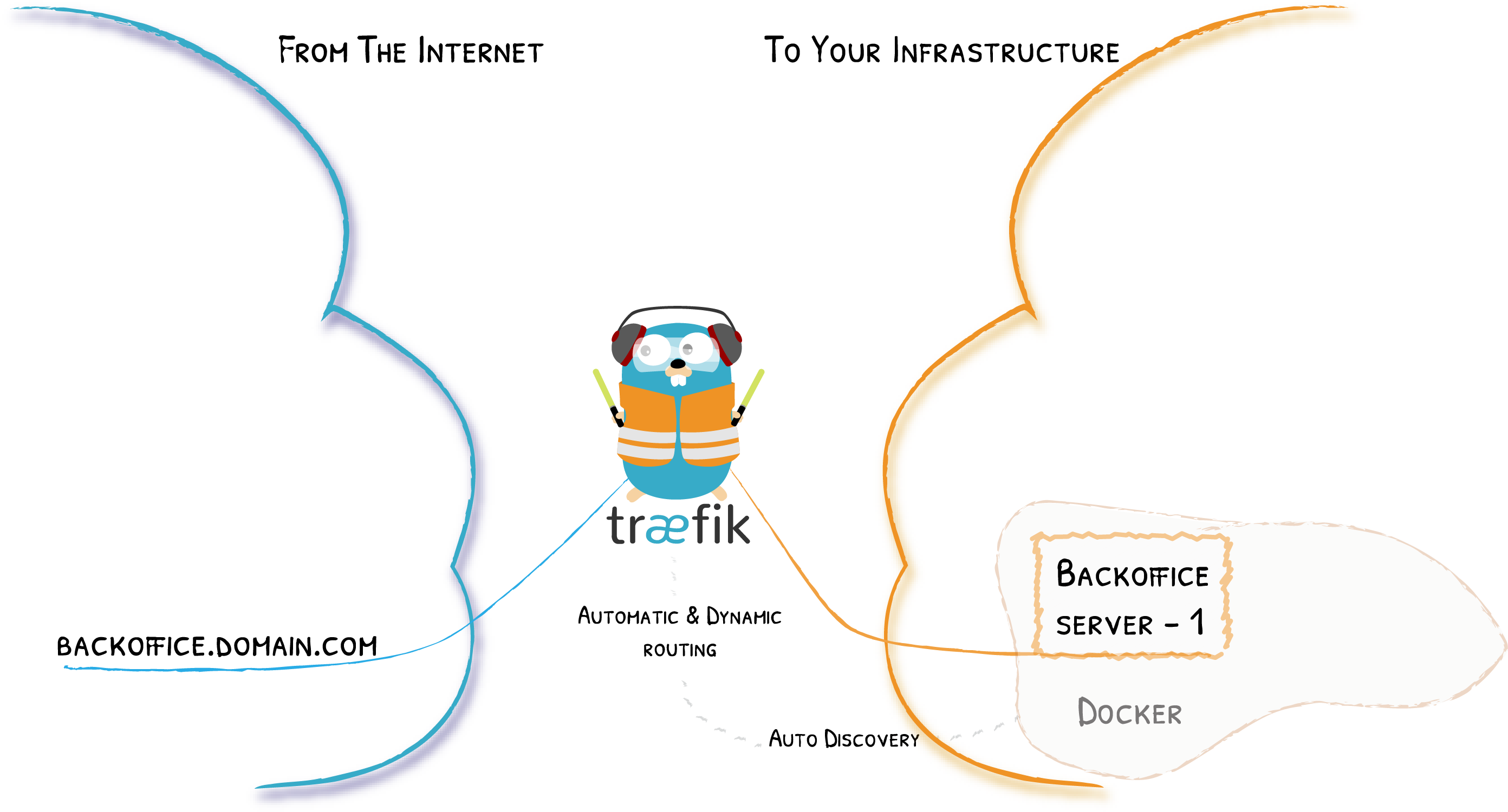
Remember the Diagram?

Let’s Simplify
Providers

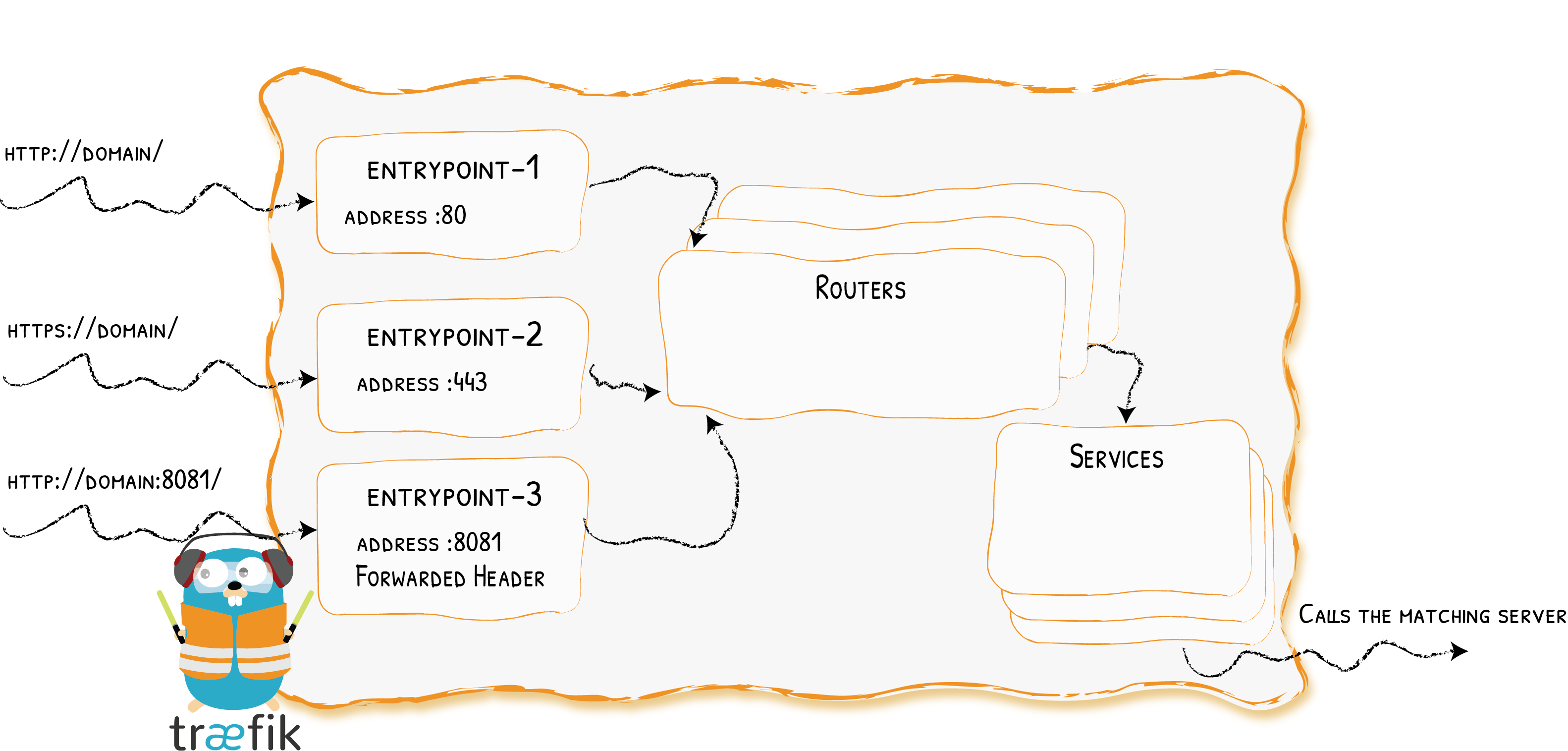
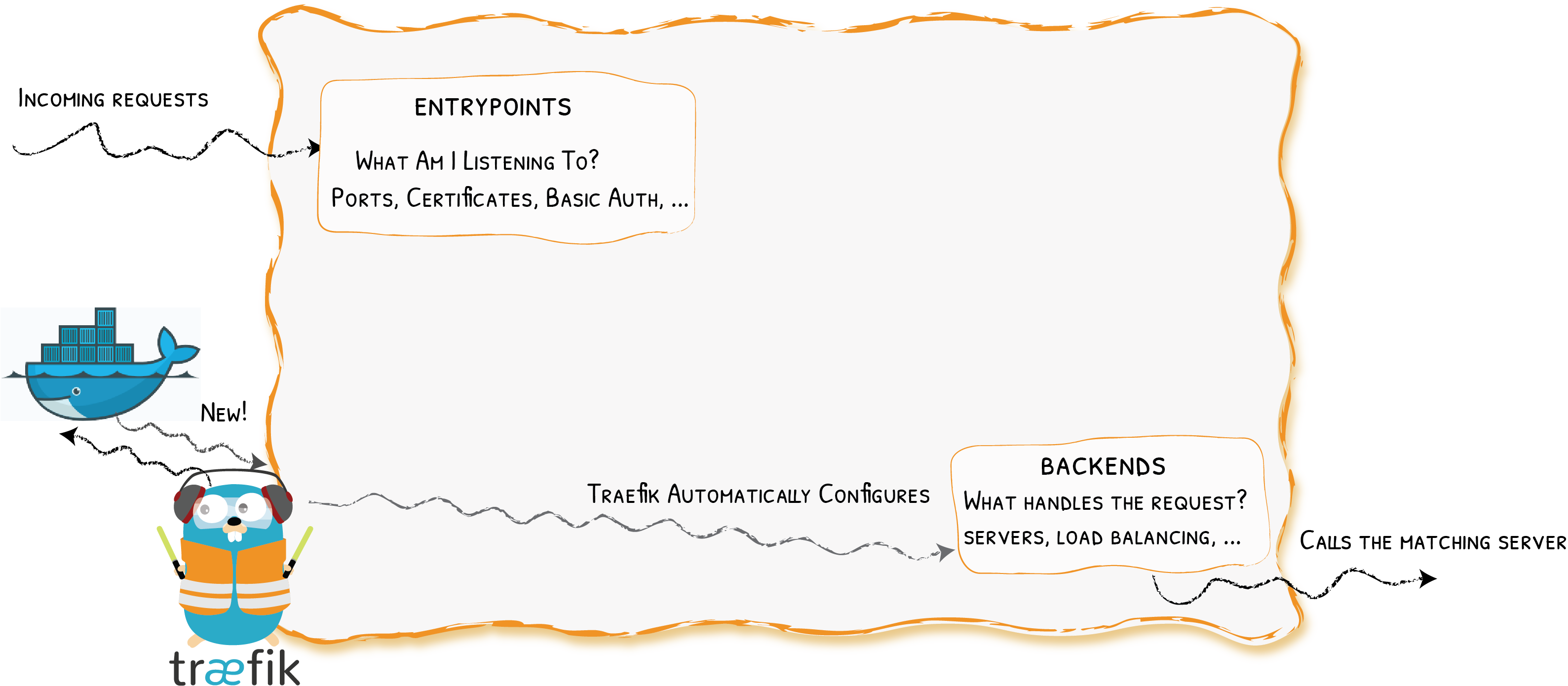
Entrypoints
Backends
Frontends
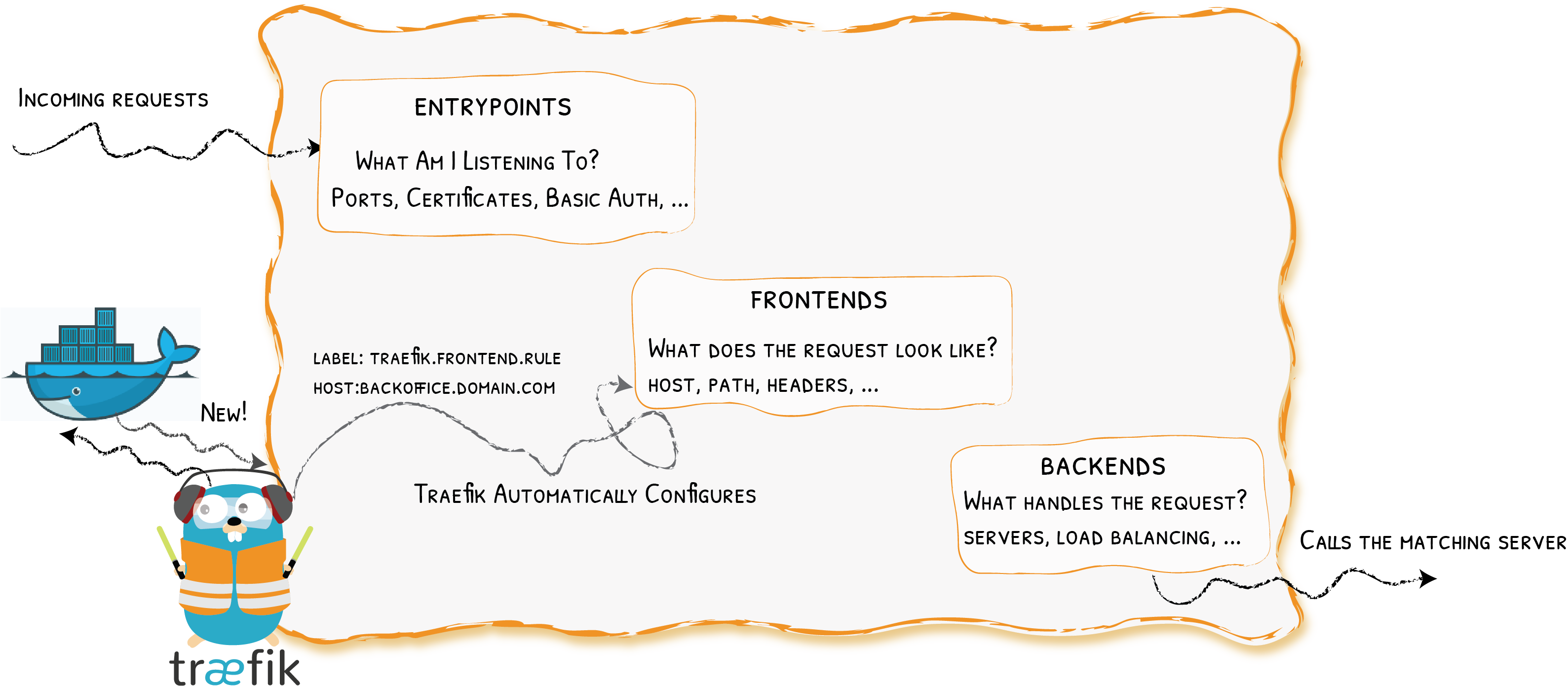
At a Glance
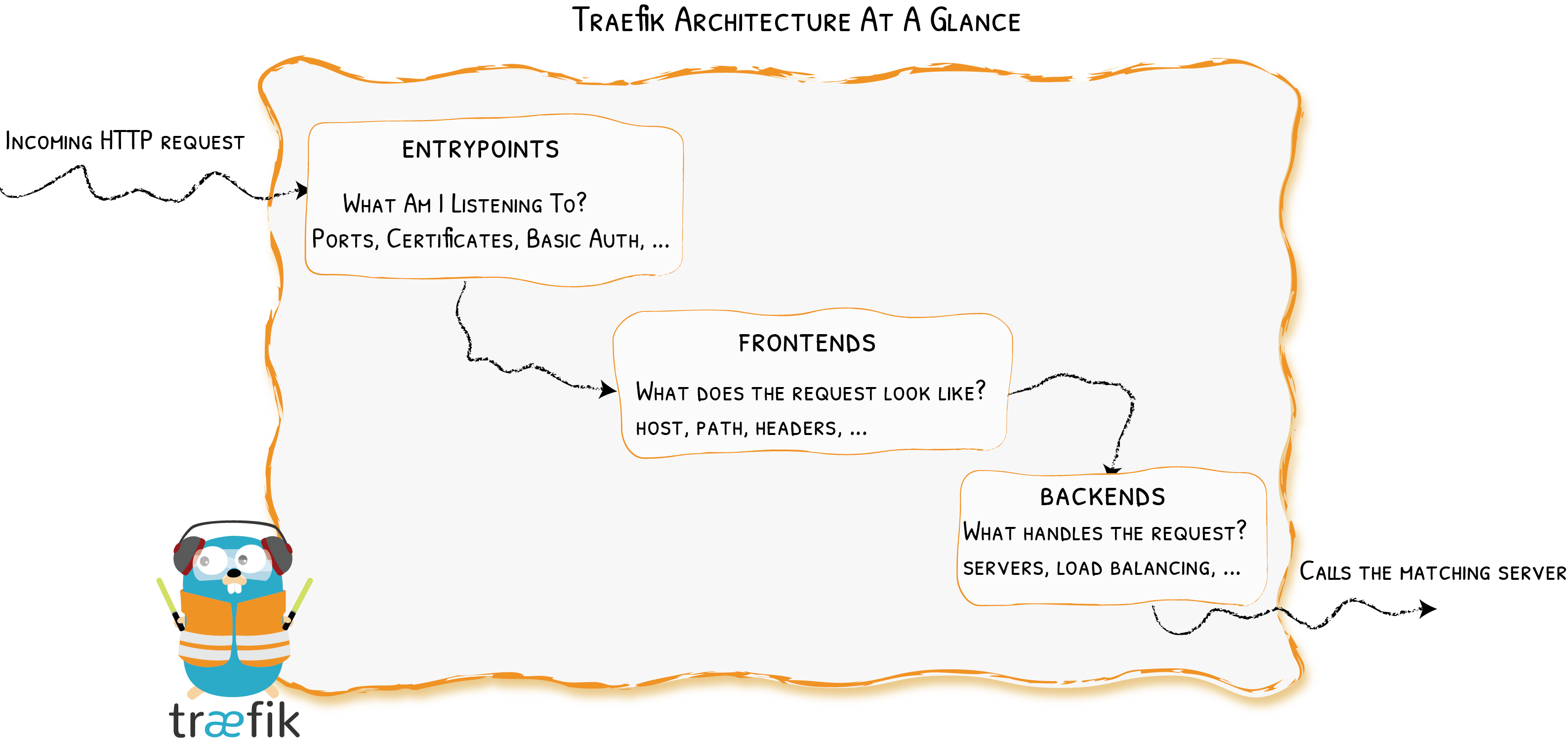
In Practice
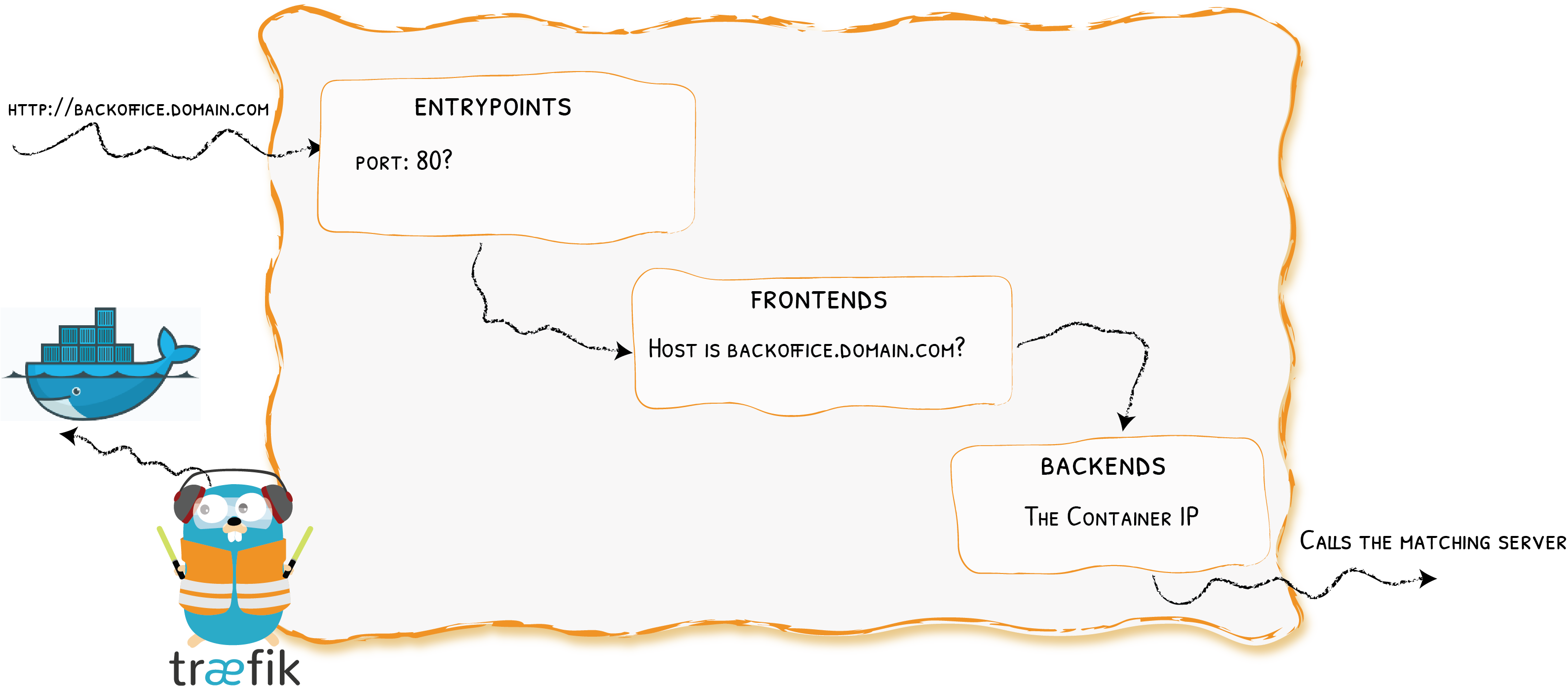
Show Me the Configuration!
Keep it Simple
With 🐳:
entrypoint:
image: traefik:v1.7
command:
- "--docker"
- "--docker.domain=mycompany.org"
- "--acme.email=ssl-admin@mycompany.org"
- "--acme.httpChallenge.entryPoint=http"
# Or you could use a TOML file with "--configFile=/etc/traefik/traefik.toml
volumes:
- /var/run/docker.sock:/var/run/docker.sockHTTPS for Everyone with Let’s Encrypt
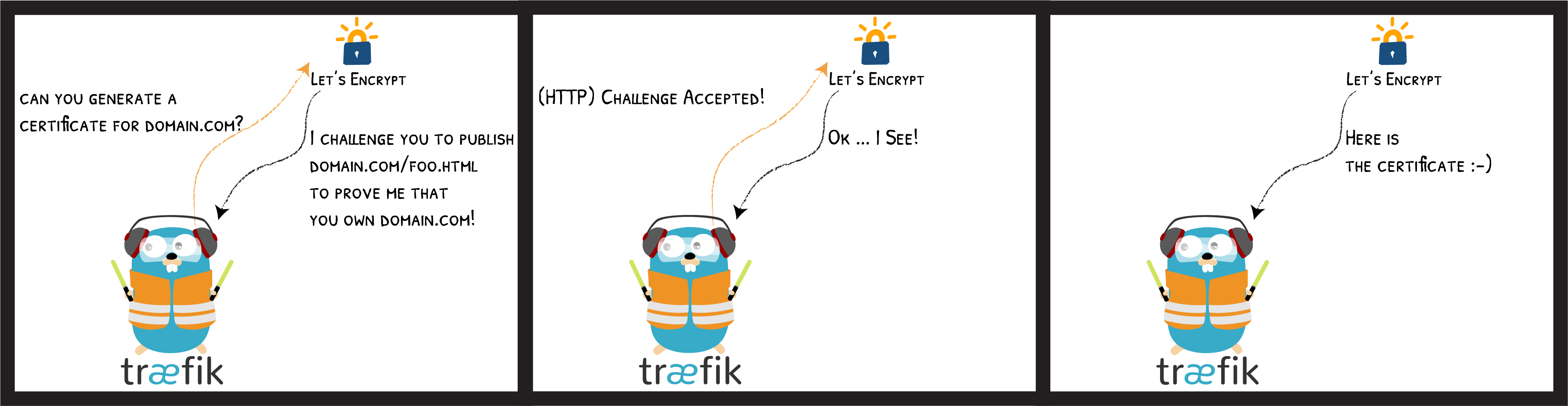
TLS, DNS and HTTP challenges supported
With 🐳: Simple backend
# https://www.mycompany.org -> http://webserver:80/
webserver:
image: nginx:alpine
labels:
- "traefik.frontend.rule=Host:www.mycompany.org"With 🐳: Context
# https://mycompany.org/jenkins -> http://jenkins:8080/jenkins
jenkins:
image: jenkins/jenkins:lts
labels:
- "traefik.frontend.rule=PathPrefix:/jenkins"
- "traefik.port=8080" # Because 50000 is also exposed
environment:
- JENKINS_OPTS=--prefix=/jenkinsWith 🐳: Rewrites
# https://mycompany.org/gitserver -> http://gitserver:3000/
gitserver:
image: gitea/gitea:1.5
labels:
- "traefik.frontend.rule=PathPrefixStrip:/gitserver"
- "traefik.port=3000" # Because 22 is also exposedWith 🐳: Websockets
# https://mycompany.org/webterminal -> http://webterminal:7681/
webterminal:
image: tsl0922/ttyd
labels:
- "traefik.frontend.rule=PathPrefixStrip:/webterminal"
expose:
- "7681"Traefik with ⎈
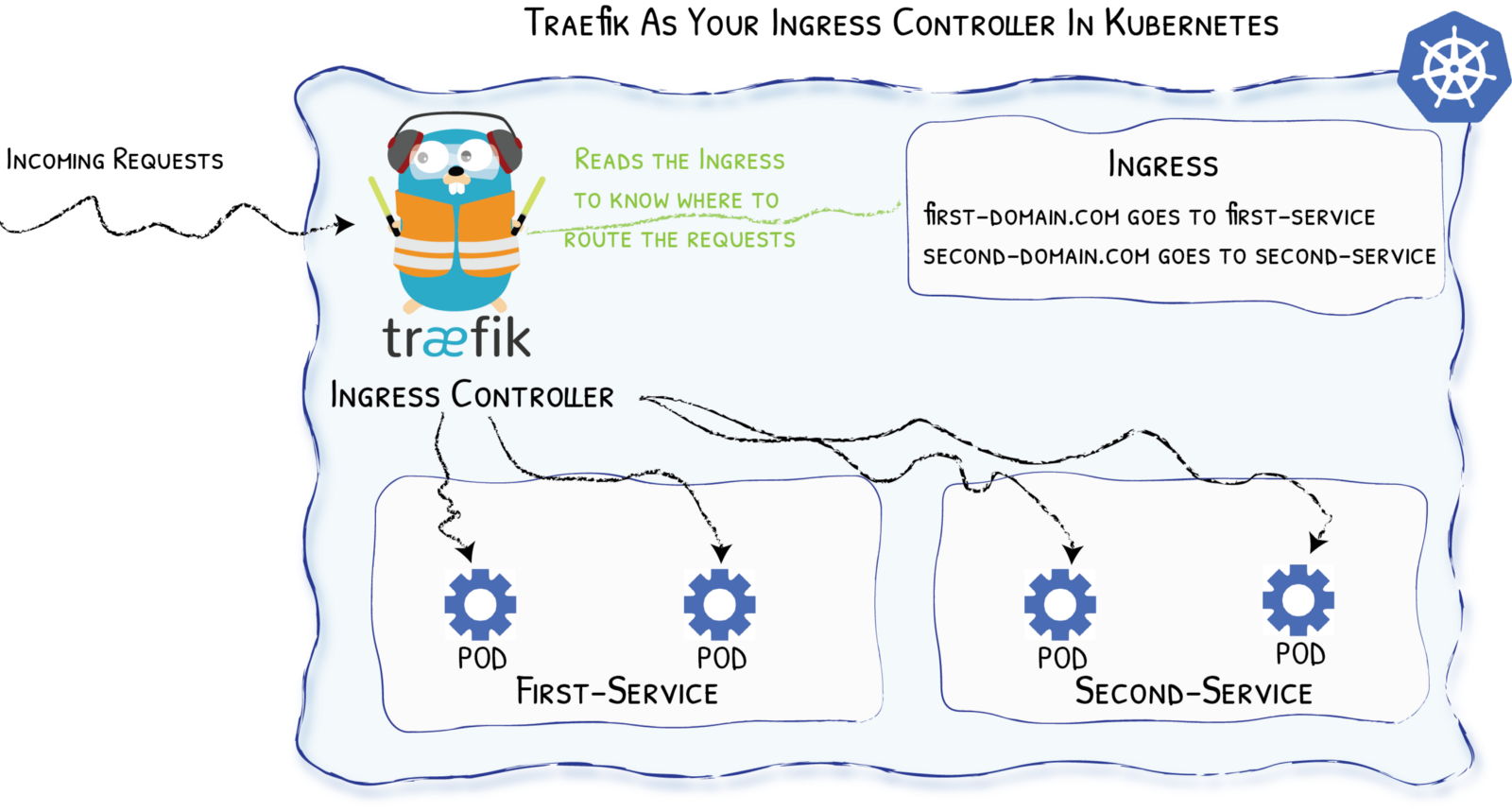
Diagram from https://medium.com/@geraldcroes
Did you say YAML?
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
annotations:
# kubernetes.io/ingress.class: 'nginx'
kubernetes.io/ingress.class: 'traefik'
spec:
rules:
- host: mycompany.org
http:
paths:
- path: "/whoami"
backend:
serviceName: whoami
servicePort: 80We Missed Talking About …

The Herd

You came to the wrong neighbour
Traefik comes in Herd
High Availability
Security
Scalability
As Simple As Traefik
Install it:
# Cluster Installation
traefikeectl install \
--licensekey="SuperSecretLicence" \
--dashboard \
--kubernetes # Or --swarmConfigure it:
# Routing Configuration, same as Traefik's
traefikeectl deploy \
--acme.email=ssl-admin@mycompany.org
--acme.tlsChallenge
...Early (Free) Access
But
What About Open Source?
Revamped Documentation
Clarified Concepts
Expressive Routing Rule Syntax
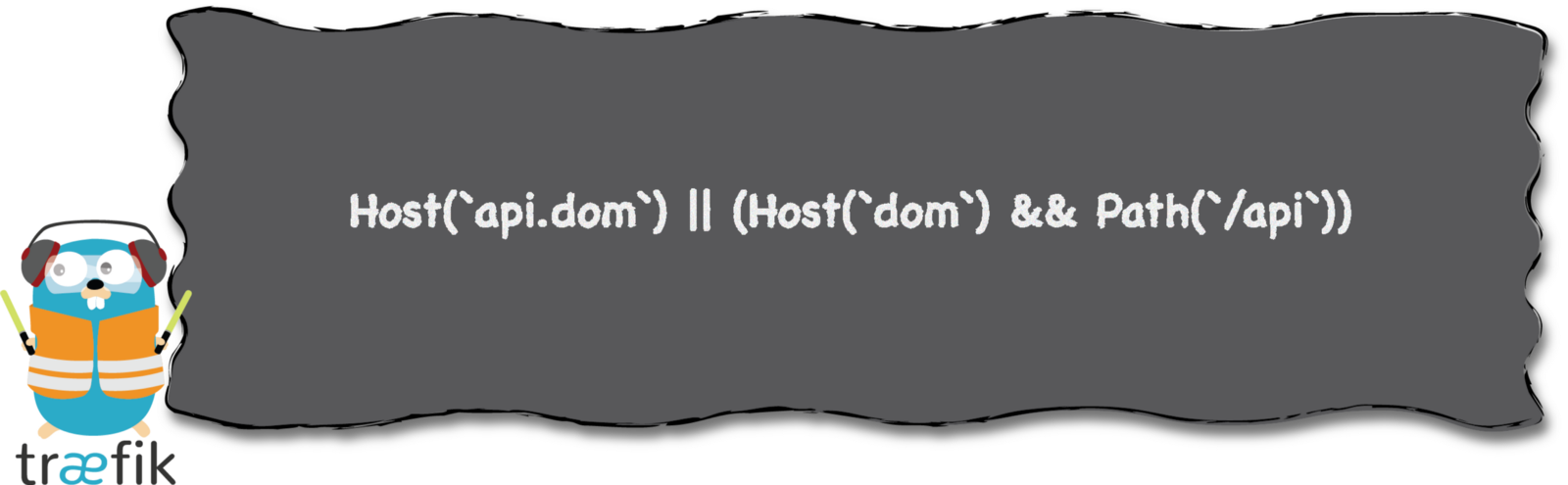
# Send both requests to backend service:
# https://api.mycompany.com/v2
# https://api-v2.mycompany.com
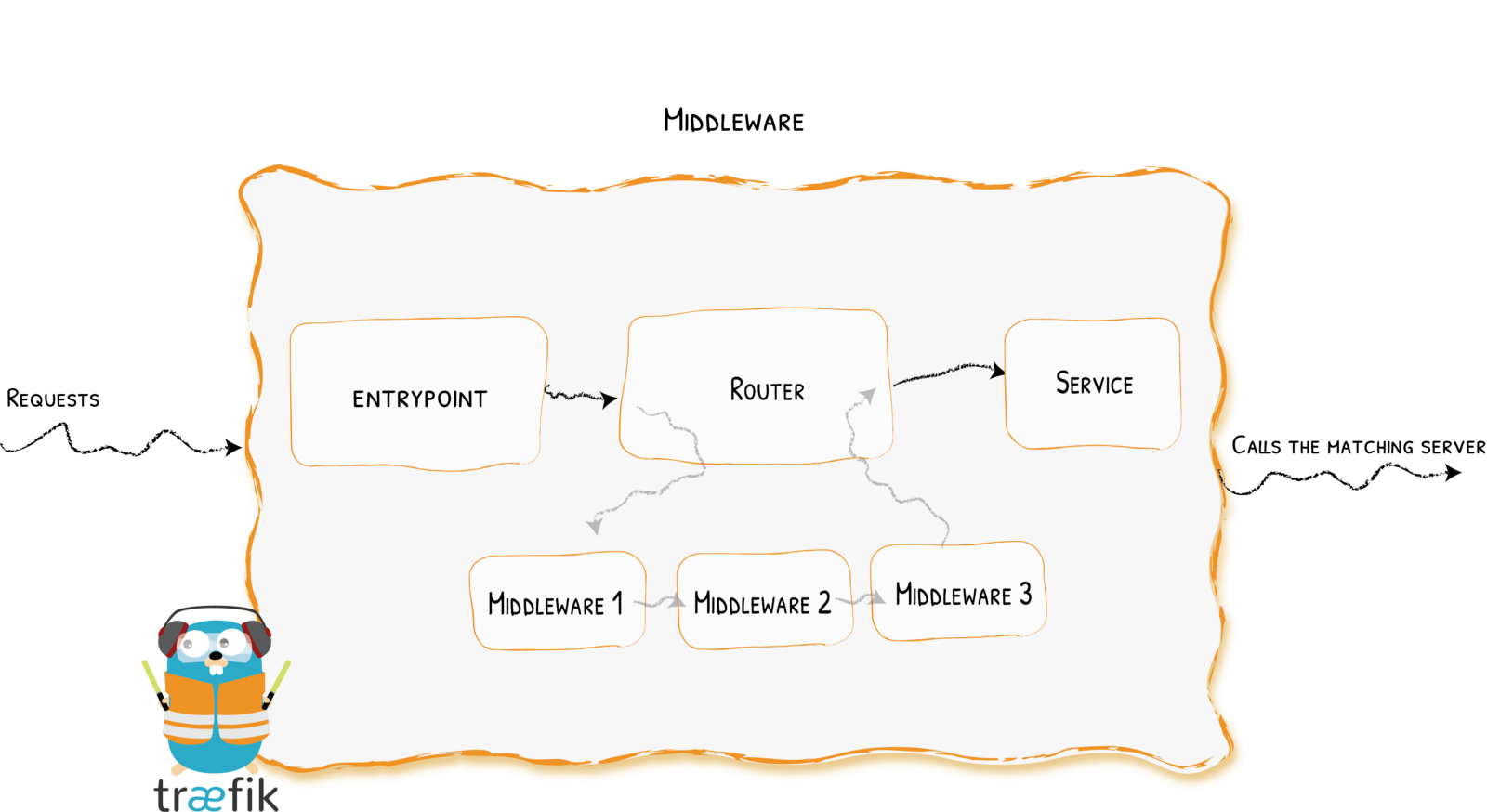
rule=(Host('api.mycompany.com') && PathPrefix('/v2')) || Host('api-v2.mycompany.com')Middlewares
⎈ CRD - Custom Resources Definition
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
spec:
entrypoints:
- web
- web-secure
routes:
- match: Host(`traefik.io`) && PathPrefix(`/foo`)
kind: Rule
services:
- name: whoami1
port: 80
strategy: RoundRobin
middlewares:
- name: stripprefix
- match: Host(`containo.us`) && Method(`POST`)
kind: Rule
services:
- name: whoami2
port: 80
tls:
secretName: supersecret
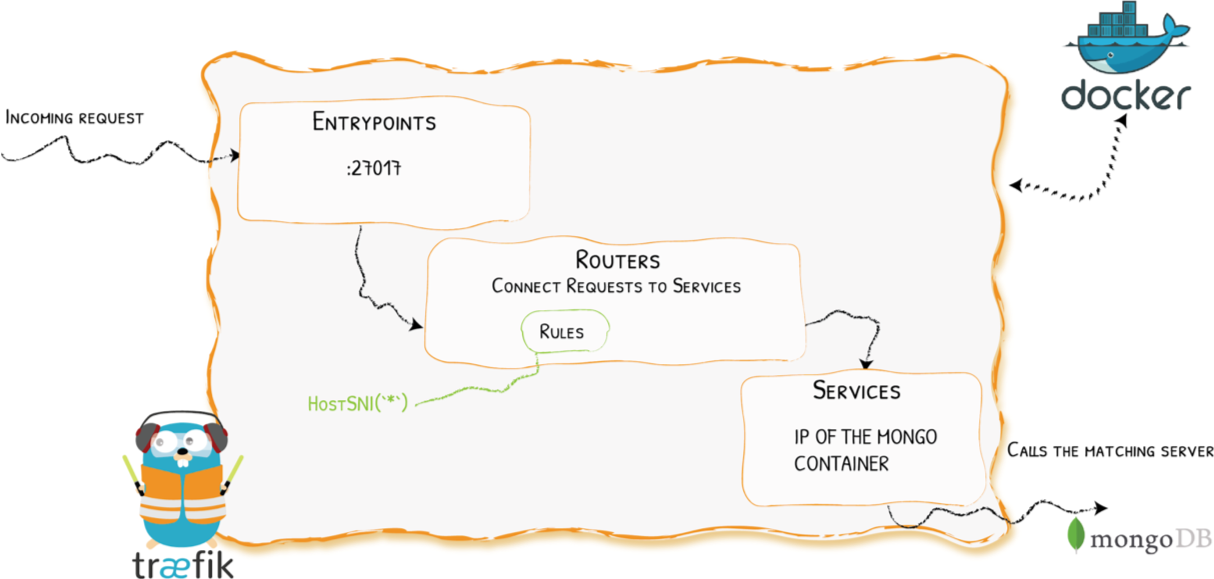
Demo 1 - Straightforward TCP Routing
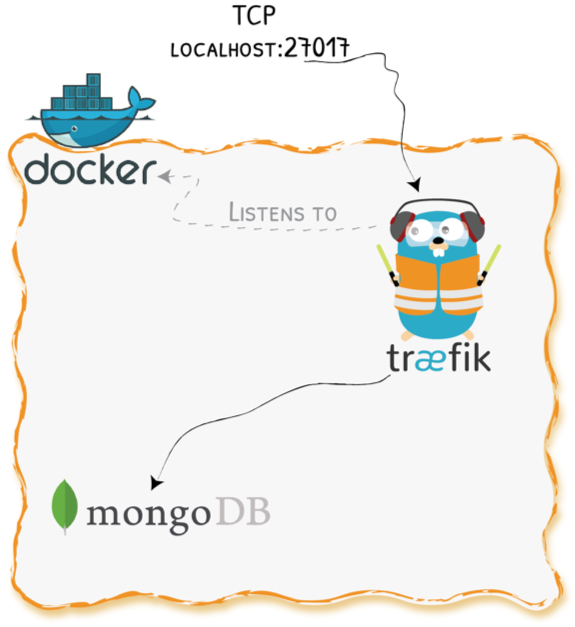
Demo 1 - Configuration
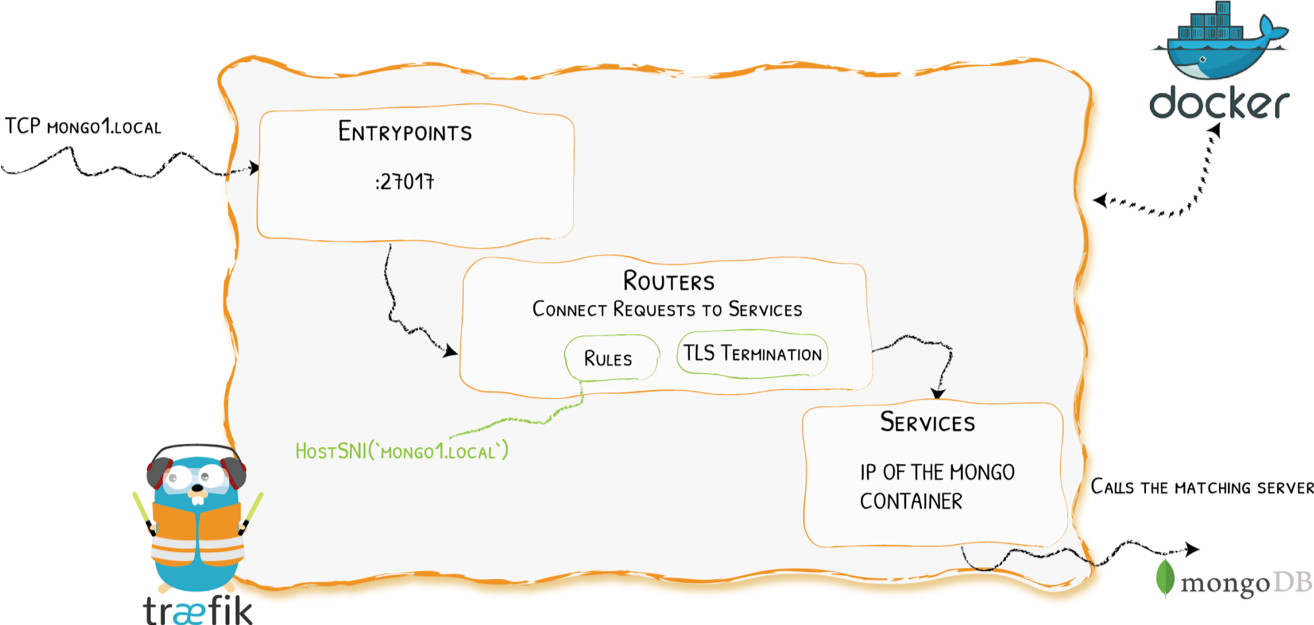
Demo 2 - Let’s Add TLS to TCP with Traefik
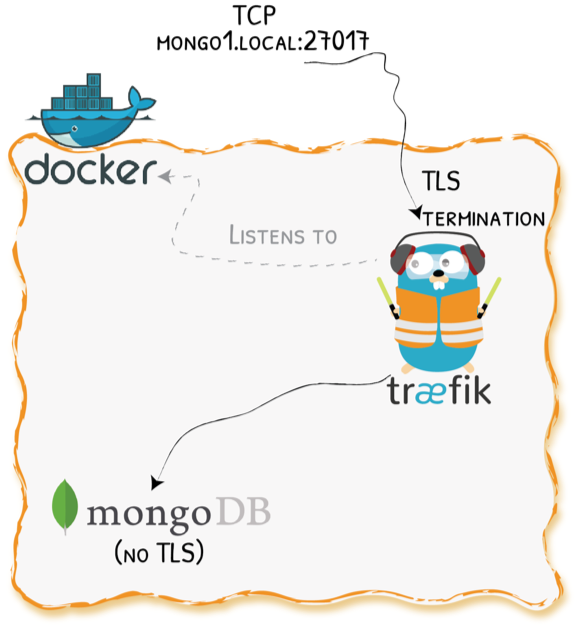
Demo 2 - Configuration
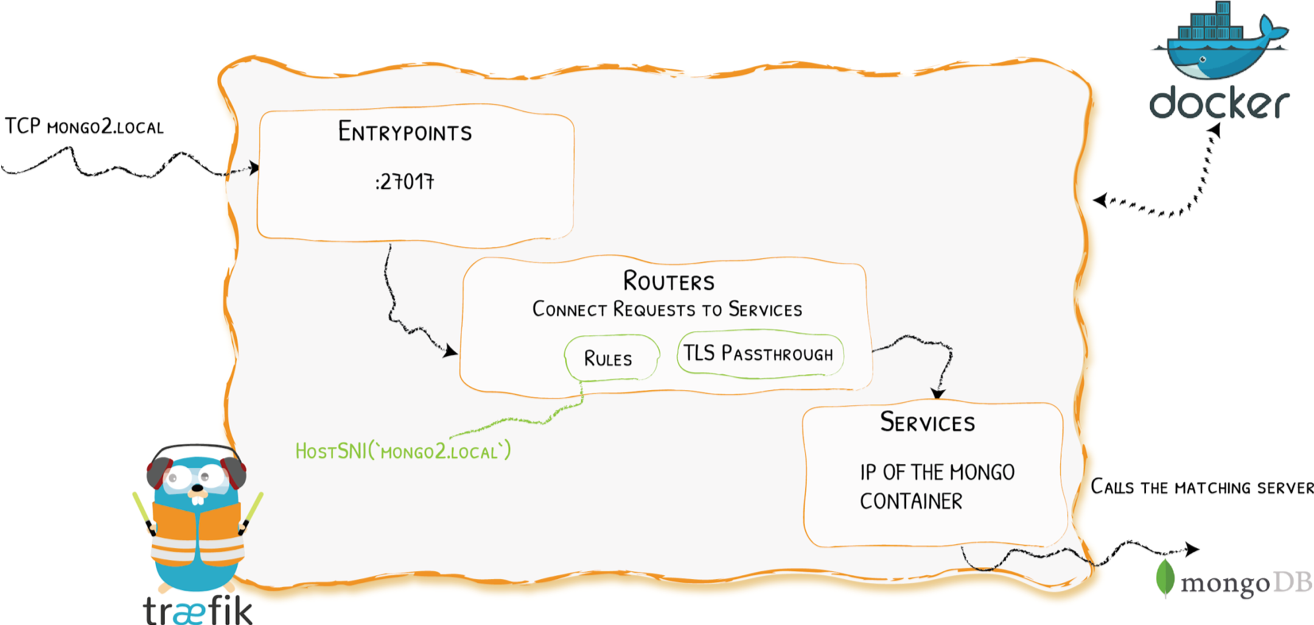
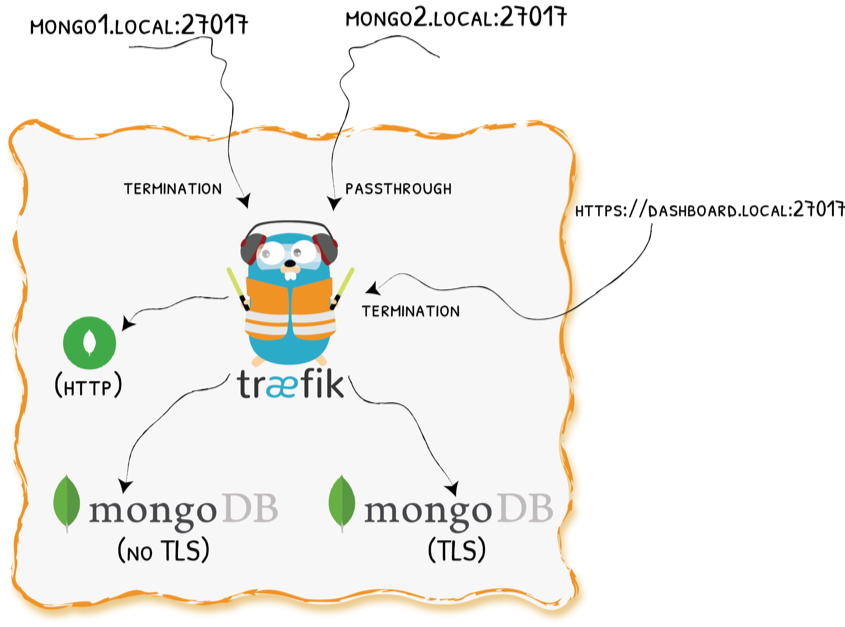
Demo 3 - SNI Routing + TLS Passthrough
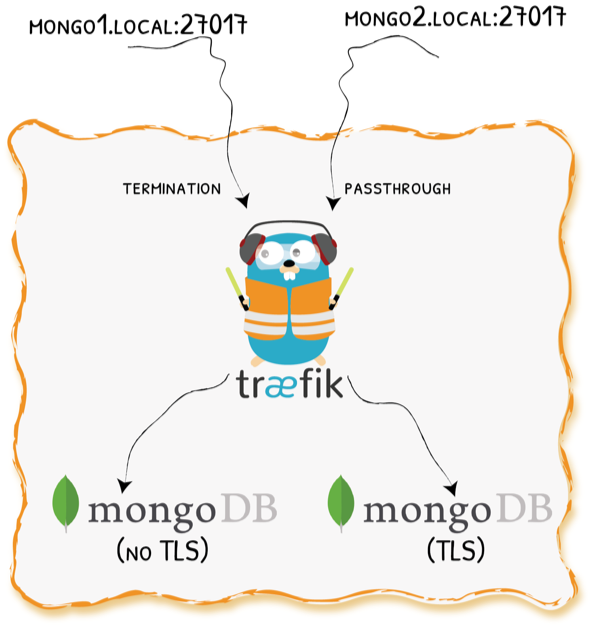
Demo 3 - Configuration
Demo 4 - Muxing HTTPS and TCP on the Same Port
More to come
New WebUI
Newmetrics
UDP
YAML
TLS stores & options
Canary
More info
We have
stickers!
Thank you!
