# SSH Access OK with the domain name
ssh -i "${SUPER_SECRET_KEY}" ubuntu@"demo.containous.cloud"
# Docker and docker-compose installed
ubuntu@${VM_IP}:~$ docker version
Client:
Version: 18.09.1
...
ubuntu@${VM_IP}:~$ docker-compose version
docker-compose version 1.23.2, build 1110ad01
...Traefik:
Keep the Routing Simple


How to use these slides?
Browse the slides: Use the arrows
Change chapter: Left/Right arrows
Next or previous slide: Top and bottom arrows
Overview of the slides: keyboard’s shortcut "o"
Speaker mode (and notes): keyboard’s shortcut "s"
Whoami
Damien DUPORTAL:
Træfik's Developer Advocate @ Containous

Containous
We Believe in Open Source
We Deliver Traefik
Commercial Support for Traefik
12 people, 90% technical experts

Why Traefik?

Evolution of Software Design
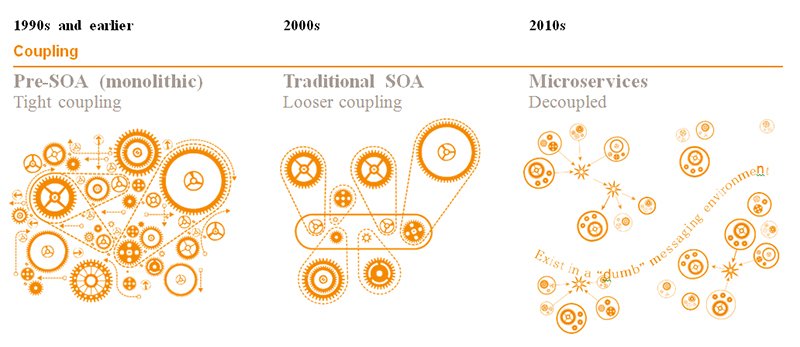
The Premise of Microservices…

…and What Happens

Where is the Service?
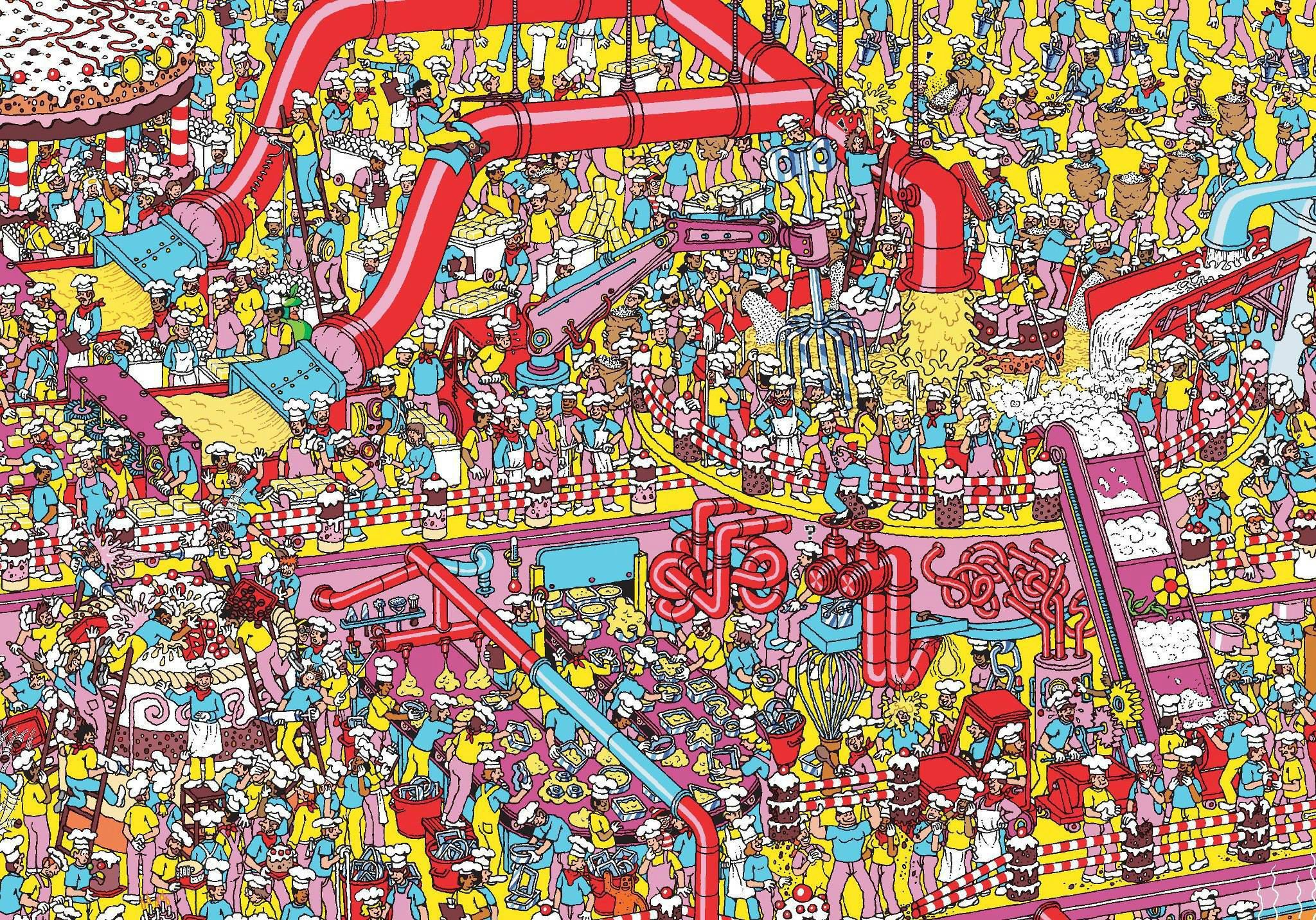
Tools of the Trade













What If I Told You?

That You Don’t Have to Write This Configuration File…?
Here Comes Traefik!
The Shack

The Shack
We want a server in Amazon EC2 cloud:
to host our own SCM Server,
and our own Continous Integration,
and a static web site,
and a "web" command line.
Infrastructure Setup
An AWS EC2 VM with a public IP
${VM_IP}and SSH accessA domain name
${PUBLIC_DOMAIN}pointing to${VM_IP}Docker and docker-compose for services
Infrastructure Setup Check
Reality Check
Traefik
Traefik Setup
Step 1: Compose file in
/home/ubuntu/meetup/docker-compose.yml:version: '2.4' services: edge: image: traefik:1.7.7 command: - "--docker" # Tells Traefik to listen to docker ports: - "80:80" # The HTTP port - "443:443" # The HTTPS port volumes: # To communicate with the Docker Engine - /var/run/docker.sock:/var/run/docker.sockStep 2: Start the stack
$ docker-compose up -d
Reality Check
It’s good: we have an HTTP answer!
Simple Web Server
Goal
We want to host a static webserver behind Traefik
Problem
How to tell Traefik to route requests to the web server?
http://demo.containous.cloud/index.html
-> Traefik
-> http://<Webserver Private IP>/index.htmlThe Web Server Setup
Step 1: web server in Compose. Check the
labels:
web:
build: ./web/
labels:
- "traefik.frontend.rule=Host:demo.containous.cloud"Step 2: Start the Web Server:
docker-compose up -d webReality Check

It’s good: we have a web page!
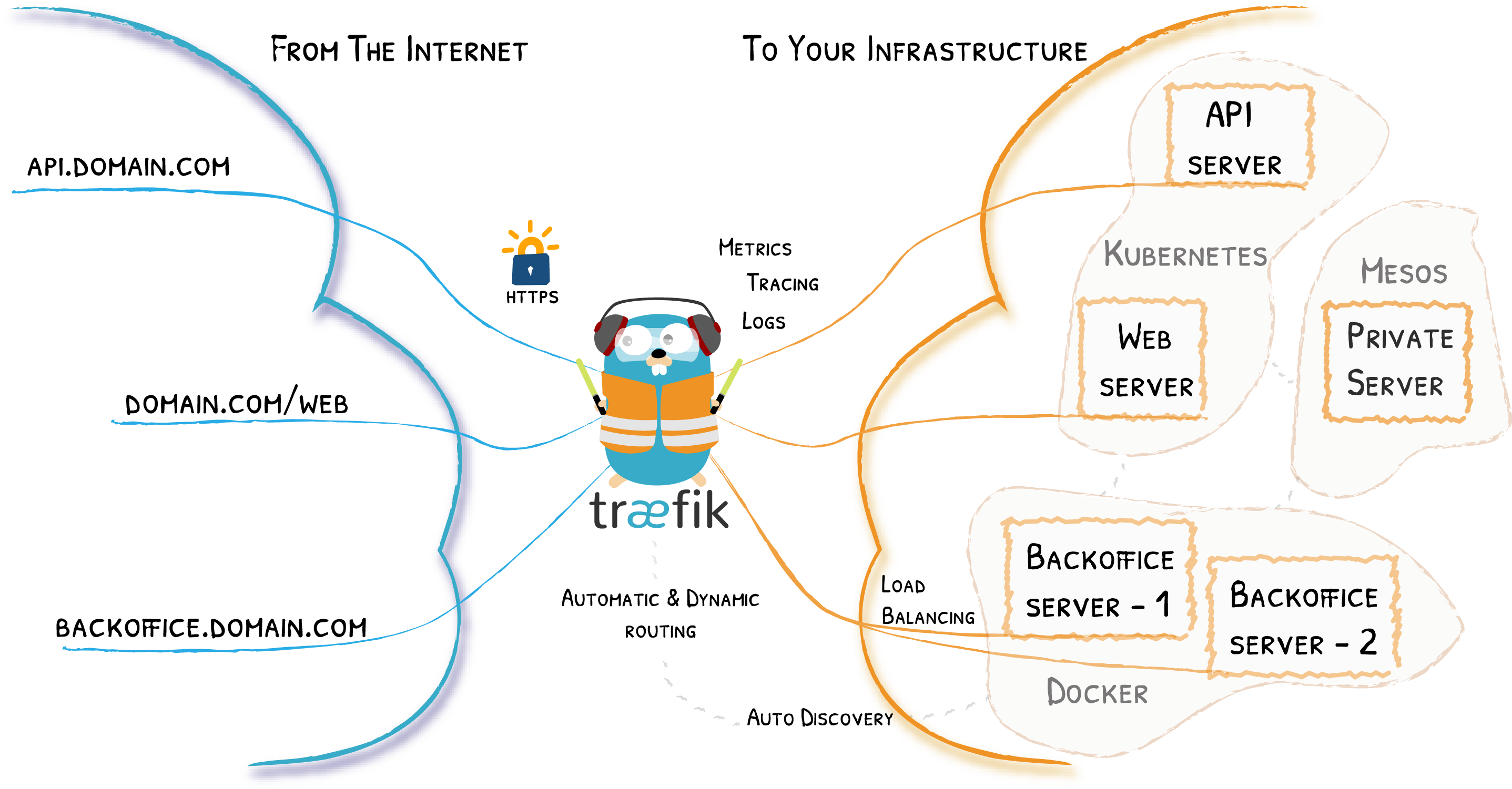
Traefik Core Concepts

Remember the Diagram?

Let’s Simplify
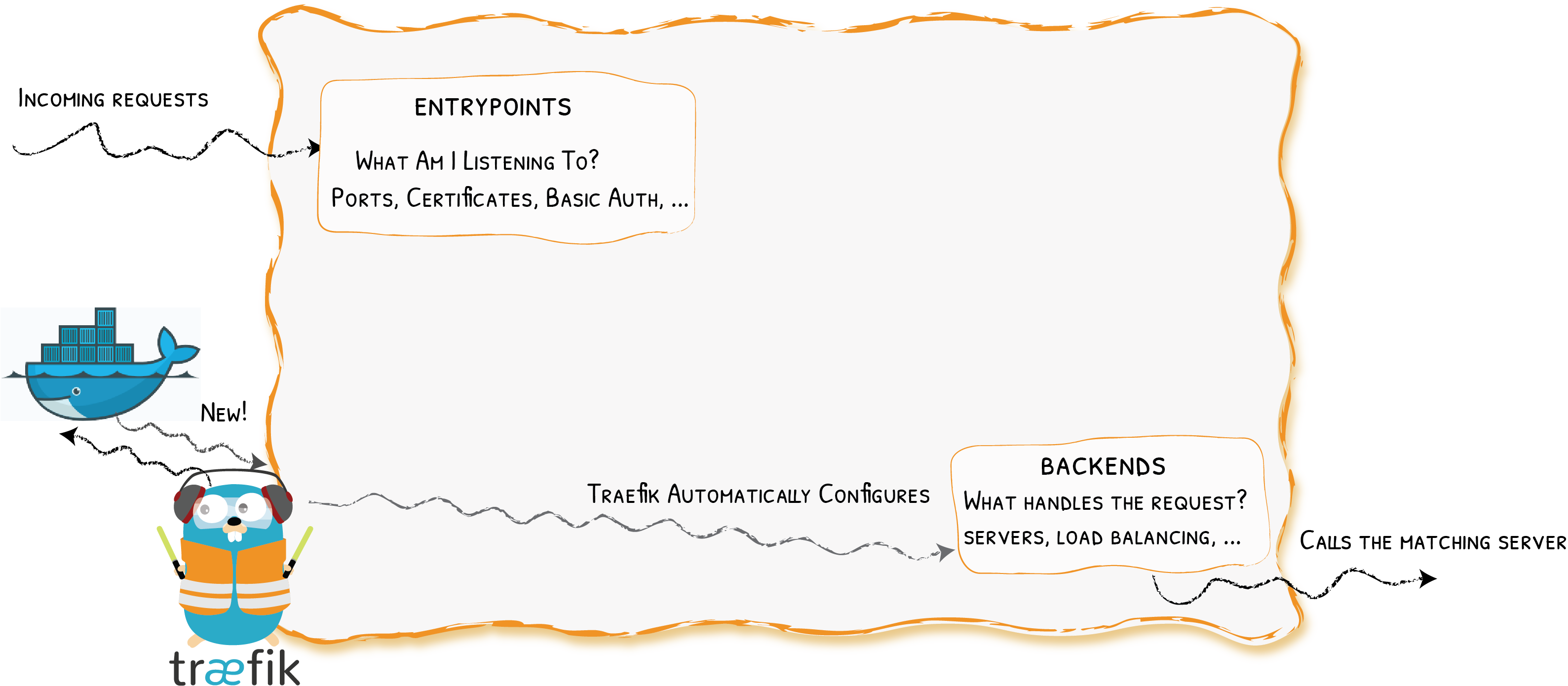
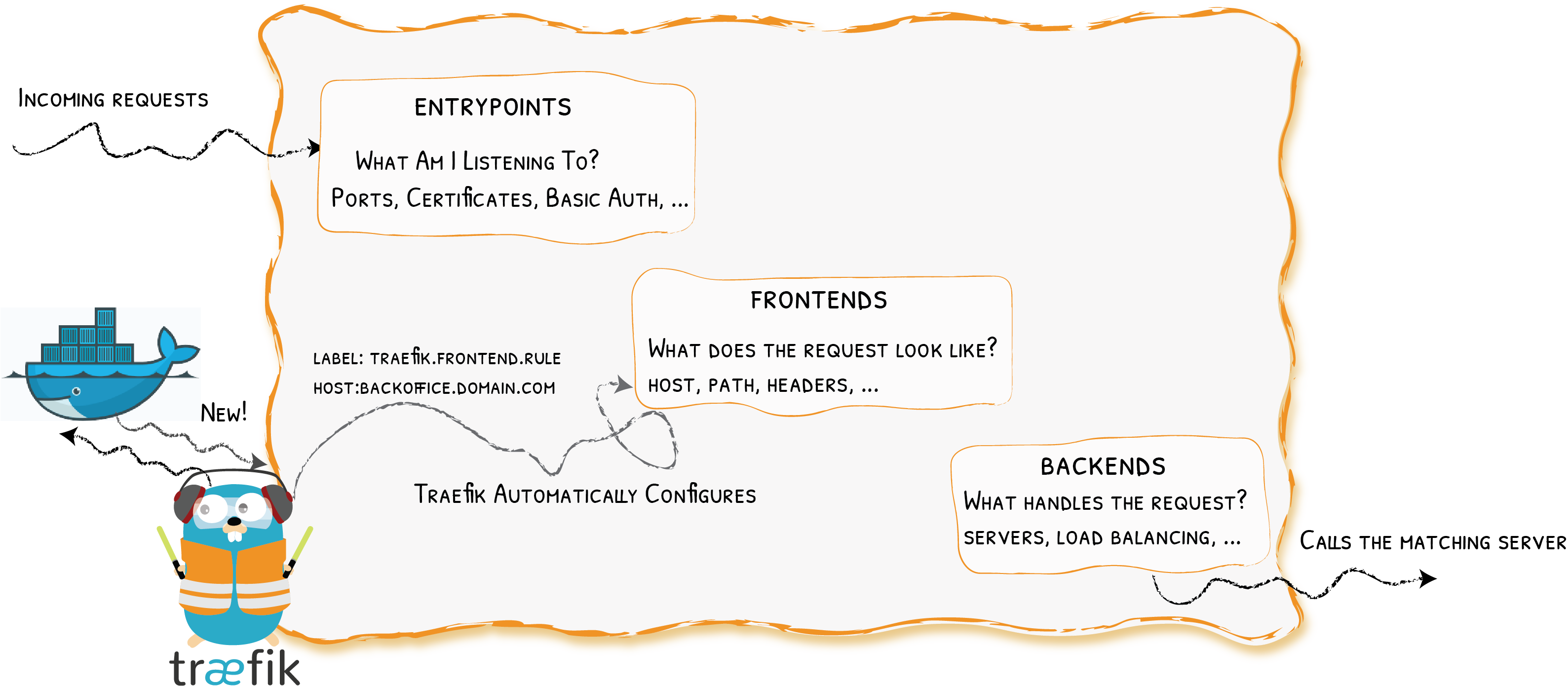
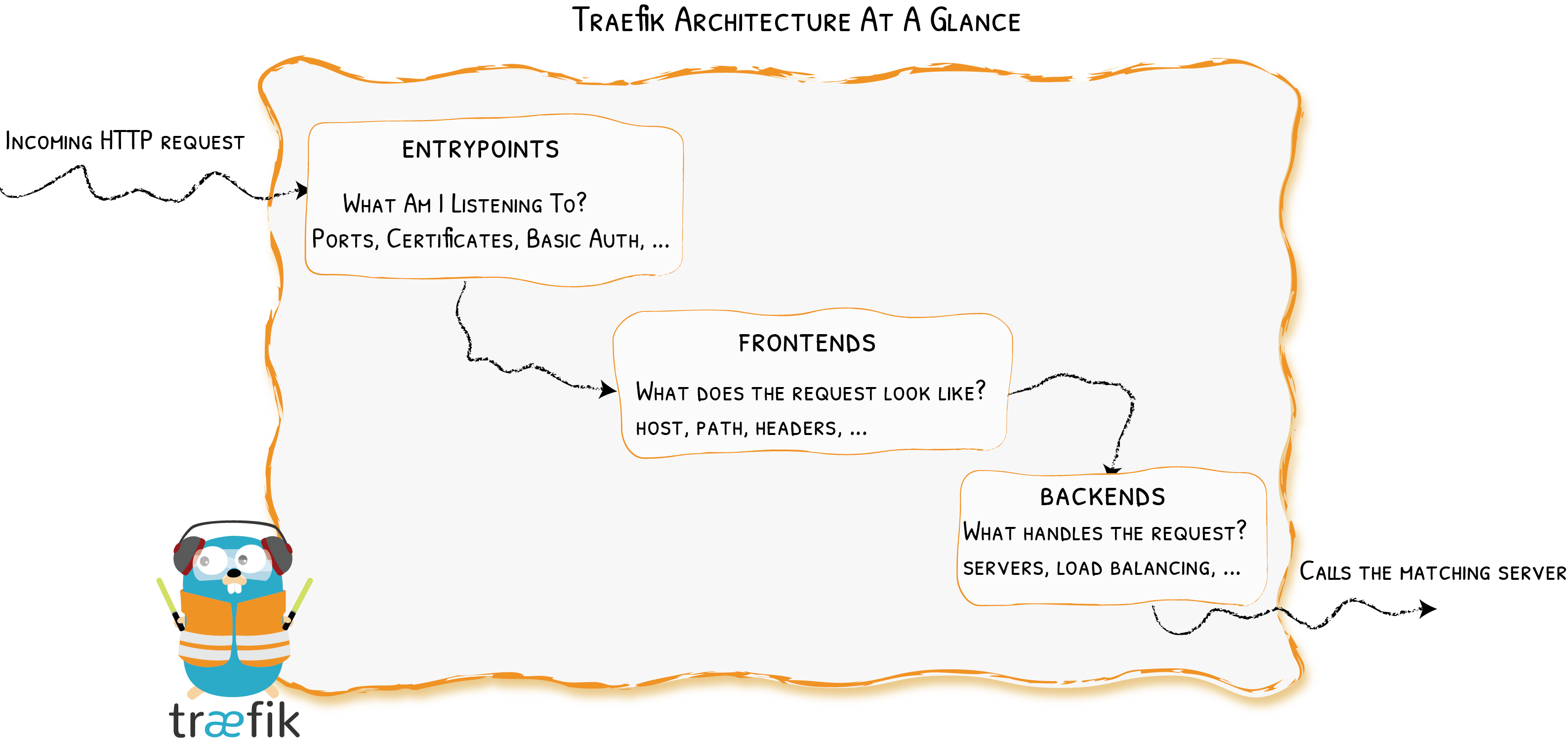
Providers

Entrypoints
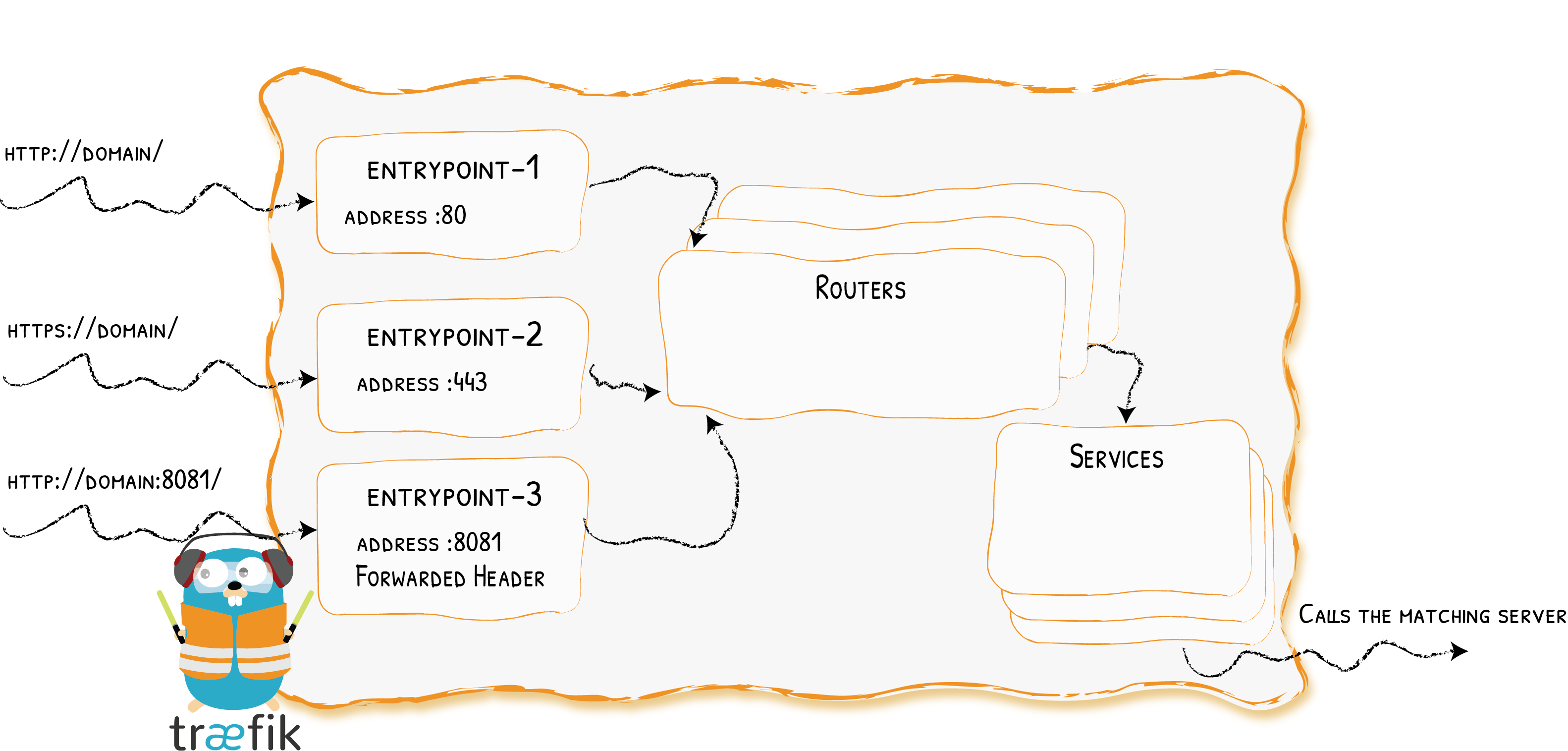
Backends
Frontends
At a Glance
Adding a CI Server
Goal
We want to host our own automation system for Continuous Integration
Let’s use Jenkins
Challenge 1/3
Problem:
Jenkins exposes 2 ports:
8080and50000. How to let Traefik know to only use8080?
Solution:
Select the port with the label
traefik.port:- "traefik.port=8080"
Challenge 2/3
Problem:
How to let Traefik know when to send requests to the Jenkins backend instead of the webserver?
http://demo.containous.cloud/jenkins/configuration -> Traefik -> http://<Jenkins Private IP>:8080/jenkins/configuration
Solution:
Change the frontend rule to use
PathPrefix:- "traefik.frontend.rule=Host:demo.containous.cloud;PathPrefix:/jenkins"
Challenge 3/3
Problem:
How to tell Jenkins to accept requests under
/jenkins?Solution:
Use the Jenkins flag
--prefix=/jenkinswith the variableJENKINS_OPTS:environment: - JENKINS_OPTS=--prefix=/jenkins
Jenkins Setup
Step 1: Edit Compose file:
jenkins:
image: jenkins/jenkins:2.150.2-alpine
expose:
- 8080
- 50000
environment:
- JENKINS_OPTS=--prefix=/jenkins
labels:
- "traefik.port=8080"
- "traefik.frontend.rule=Host:demo.containous.cloud;PathPrefix:/jenkins"Step 2: update the service
docker-compose up -d jenkinsReality Check
Click on the "Jenkins" link:
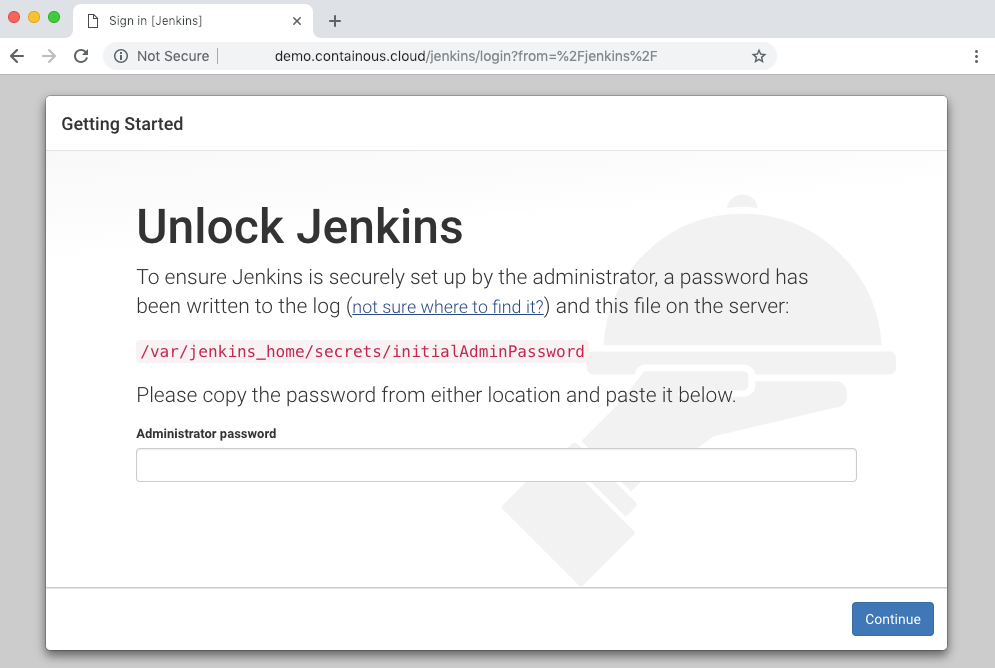
It’s good: we can setup Jenkins!
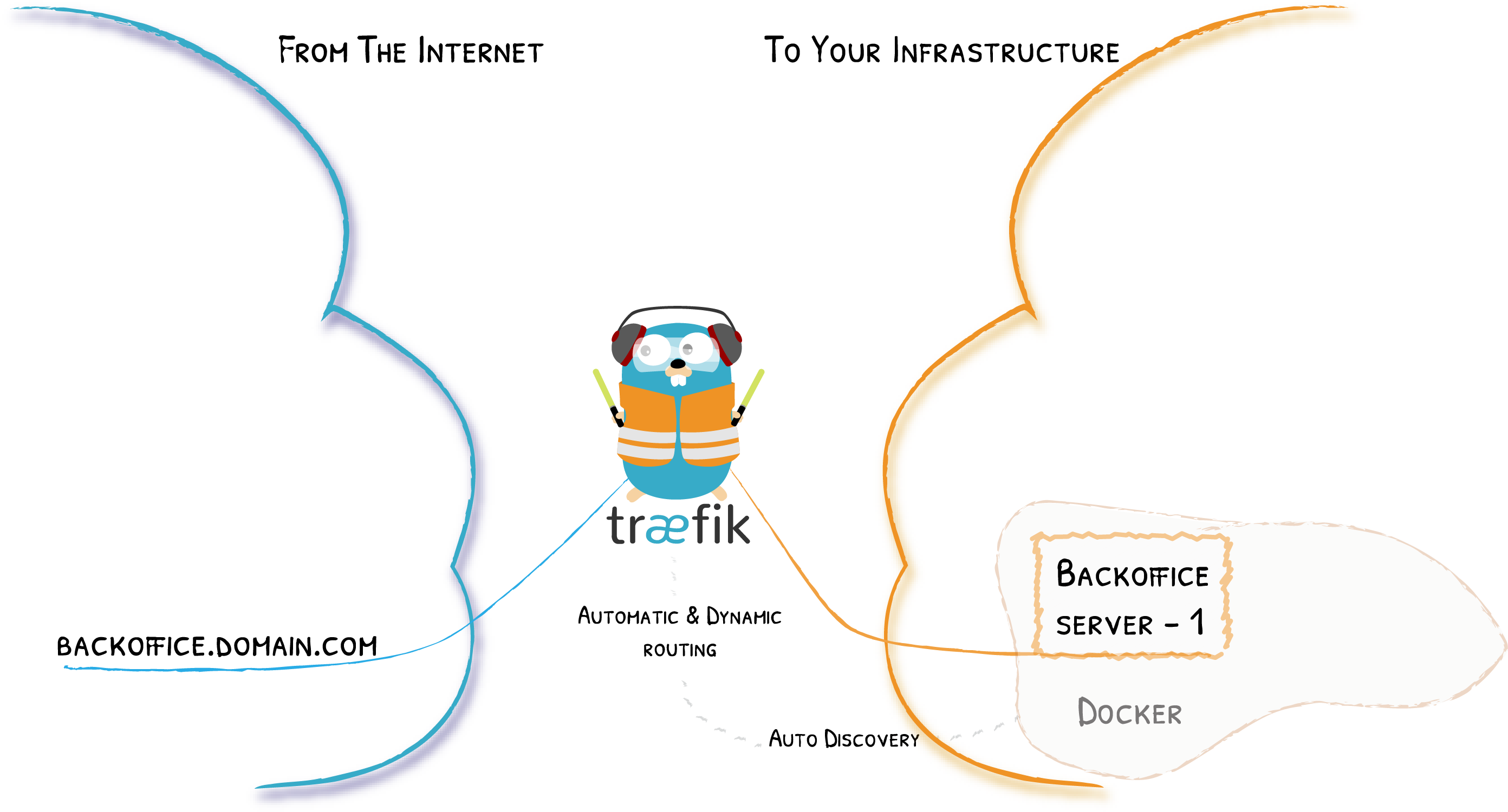
SCM: A Gitea Git Server
Goal
We want to host our own git server
Challenge
Problem:
Gitea only serves requests under
/: How to remove the prefix/gitserver?
http://demo.containous.cloud/gitserver/index.html
-> Traefik
-> http://<Gitea private IP>:3000/index.htmlSolution:
Use the Traefik’s Frontend Rule
PathPrefixStrip
- "traefik.frontend.rule=Host:demo.containous.cloud;PathPrefixStrip:/gitserver"Gitea Setup
Step 1: Edit Compose file:
gitserver:
image: gitea/gitea:latest
expose:
- "3000"
- "22"
environment:
- ROOT_URL=/gitserver
labels:
- "traefik.port=3000"
- "traefik.frontend.rule=Host:demo.containous.cloud;PathPrefixStrip:/gitserver"Step 2: create the service
docker-compose up -d gitserverReality Check
Try the "Gitea Git server" link:
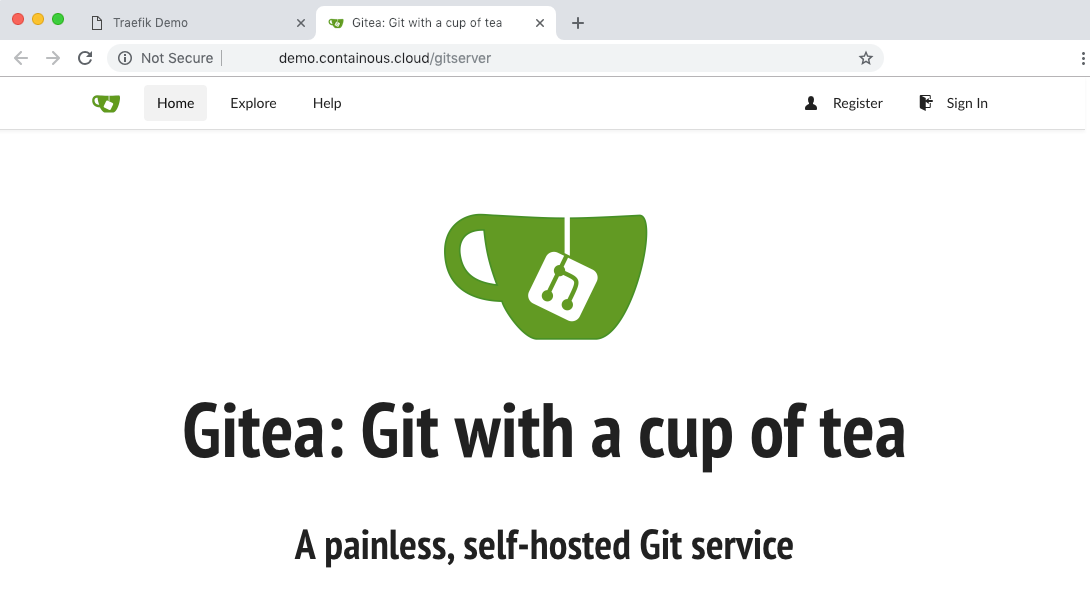
It’s good: we can setup Gitea!
A Web CLI
Goal
We want to host our own Web Command Line
Let’s use TTYD, Share your terminal over the web.
Challenge
Problem: TTYD requires Websockets
Solution:
It’s not even a problem with Traefik!
Easy Peasy!
Step 1: Edit Compose file:
ttyd:
image: tsl0922/ttyd
labels:
- "traefik.frontend.rule=Host:demo.containous.cloud;PathPrefixStrip:/ttyd"Step 2: create the service
docker-compose up -d ttydReality Check
Try the "TTYD Web Command Line" link:
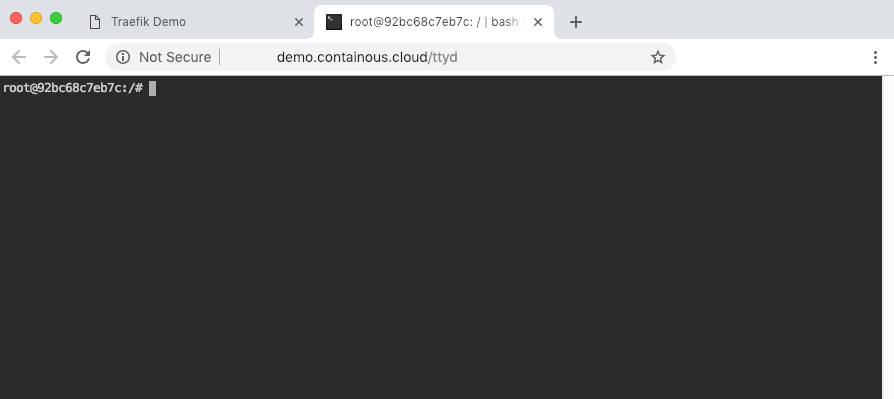
It’s good: we have our own "Dev Box" in a web browser!
HTTPS for Everyone
Goals
Use HTTPS instead of HTTP
Do NOT care about certificates and renewal
Redirect any incoming HTTP request to HTTPS:
http://demo.containous.cloud/ -> https://demo.containous.cloud/
Let’s Encrypt is a free, automated, and open Certificate Authority.
It uses the "ACME" protocol to verify that you control a given domain name and to issue you a certificate.
Problem 1/4
Problem:
How to tell Traefik to listen on port
443for HTTPS requests?
Solution:
Create a new entrypoint with the flag
--entrypoints,And the default entrypoint with
--defaultentrypoints:- "--entryPoints=Name:https Address::443 TLS" - "--defaultEntryPoints=https,http"
Problem 2/4
Problem:
How to tell Traefik to redirect request from http to https?
Solution:
Configure the new entrypoint
httpwith the flag--entrypoints:- "--entryPoints=Name:http Address::80 Redirect.EntryPoint:https"
Problem 3/4
Problem:
How to tell Traefik to use Let’s Encrypt for HTTPS?
Solution:
Configure the ACME/Let’s Encrypt provider with the flags
--acme.*:
- "--acme.entryPoint=https" # Uses LE certificates on the entrypoint "https" .
- "--acme.email=damien@containo.us" # Specifies the contact email for the certificates.
- "--acme.storage=acme.json" # Stores certificates in the file "acme.storage".
- "--acme.tlsChallenge=true" # Uses TLS Challenge.
- "--acme.onHostRule=true" # Get cert's domain names from frontend rules.ACME Challenges
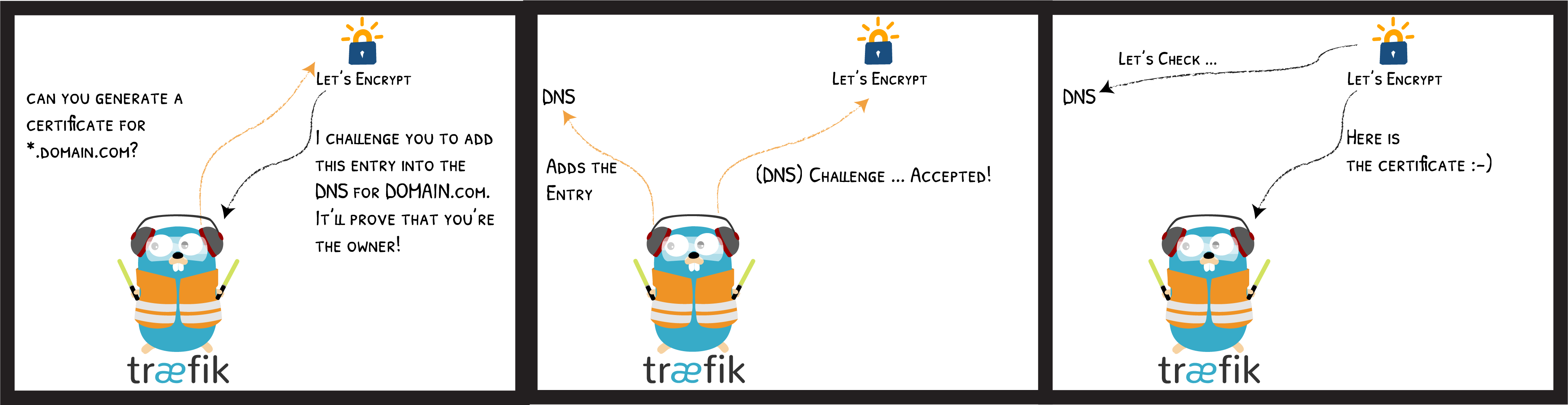
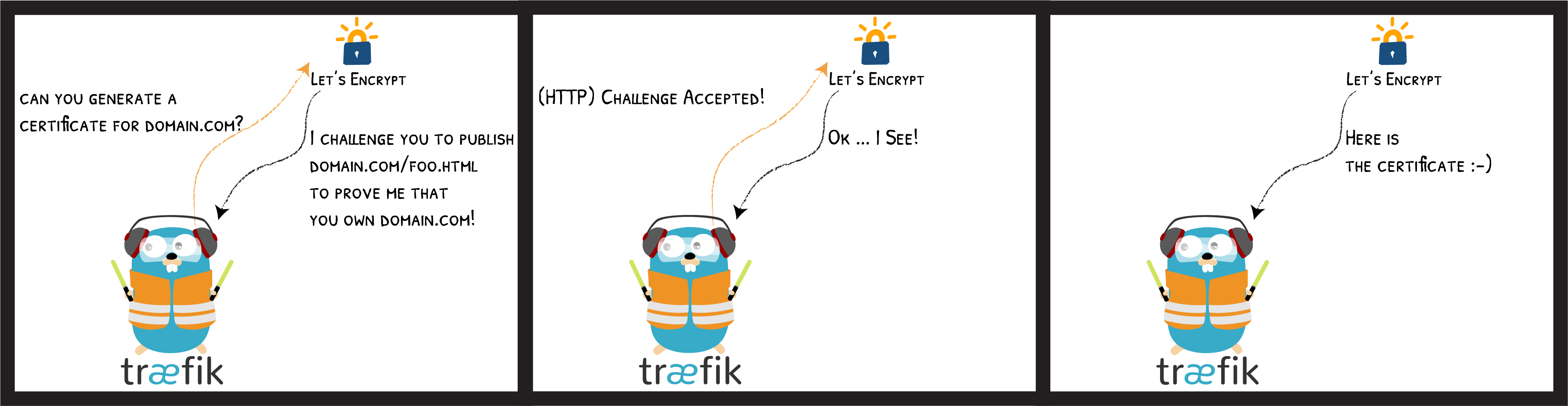
Problem 4/4
Problem:
Traefik detects itself as a docker container with a port, and tries to request a 2nd certificate for
edge.demo.containous.cloud
Solution:
Exclude Traefik’s container with the label
traefik.enable=false
Traefik Setup
Step 1: Adapt Compose file:
command: - "--entryPoints=Name:http Address::80 Redirect.EntryPoint:https" - "--entryPoints=Name:https Address::443 TLS" - "--defaultEntryPoints=https,http" - "--acme.entryPoint=https" # Uses LE certificates on the entrypoint "https" . - "--acme.email=damien@containo.us" # Specifies the contact email for the certificates. - "--acme.storage=acme.json" # Stores certificates in the file "acme.storage". - "--acme.tlsChallenge=true" # Uses TLS Challenge. - "--acme.onHostRule=true" # Get cert's domain names from frontend rules. - "--docker" labels: - "traefik.enable=false"Step 2: Update the
edgeservicedocker-compose up -d edge
Reality Check
Wait a few seconds (time to get the certificate from Let’s Encrypt) and reload the main page:
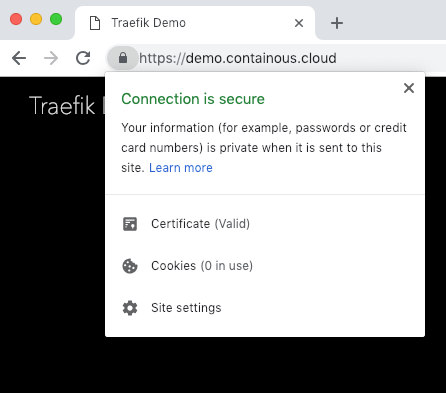
Thank You!
Find more on Traefik
Recording will be available on
You can follow us on
Source available at https://github.com/containous/slides