Traefik v2.0 & Maesh: Look Ma’, routing HTTP and TCP with no Hands!

How to use these slides?
Browse the slides: Use the arrows
Change chapter: Left/Right arrows
Next or previous slide: Top and bottom arrows
Overview of the slides: keyboard’s shortcut "o"
Speaker mode (and notes): keyboard’s shortcut "s"
Whoami
Damien DUPORTAL:
Træfik's Developer 🥑 Advocate @ Containous

Containous
We Believe in Open Source
We Deliver Traefik and Traefik Enterprise Edition
Commercial Support
30 people distributed, 90% tech

Why Traefik?

Why, Mr Anderson?
Evolution of Software Design
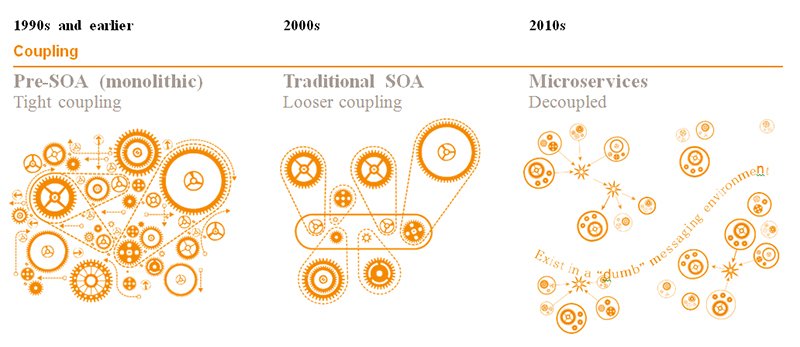
The Premise of Microservices…

…and What Happens

Where’s My Service?
Tools of the Trade













What If I Told You?

That You Don’t Have to Write This Configuration File…?
Here Comes Traefik!
Traefik Project
MIT License
Written in Go
24,000+ ⭐ 1B+ ⬇️ 400+ 👷
Created in 2015, 4Y 🎂
Current stable branch:
v2.0
Traefik 2.0 Quick Overview
Revamped Documentation
Clarified Concepts
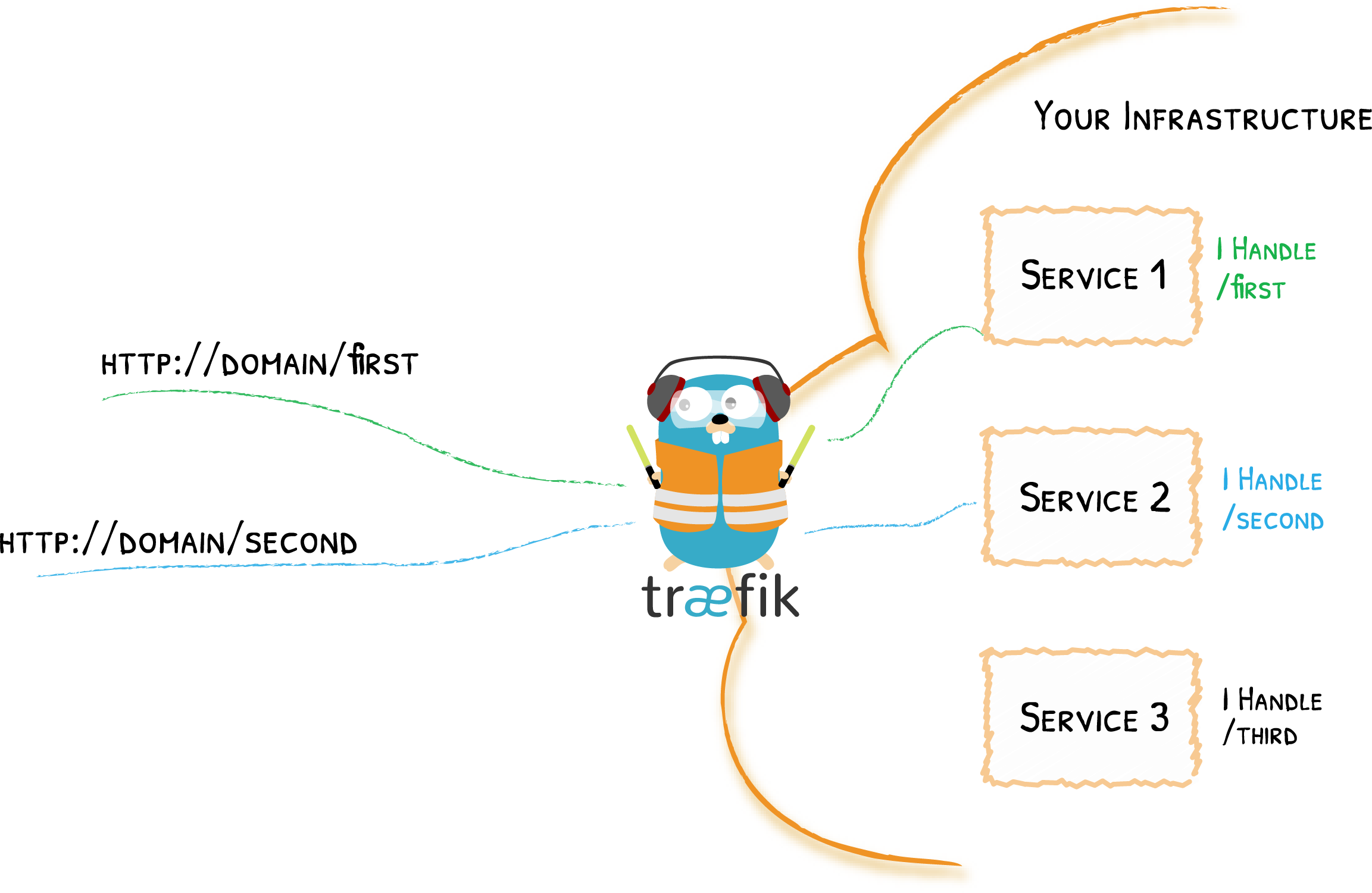
Expressive Routing Rule Syntax
Middlewares
TCP Support
Canary / Mirroring
And so Much More…
Traefik (v2.0) Core Concepts

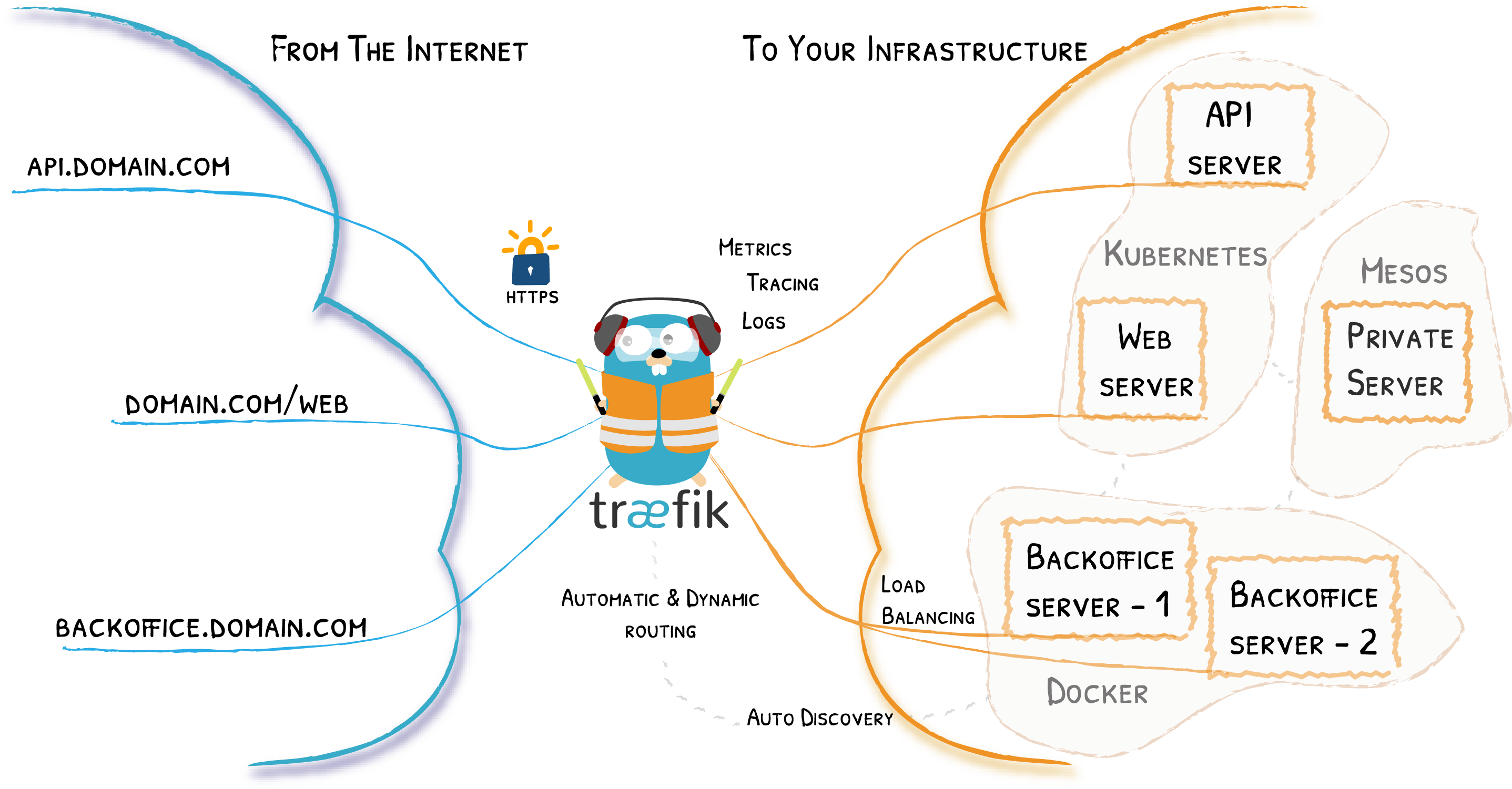
Traefik is an Edge Router
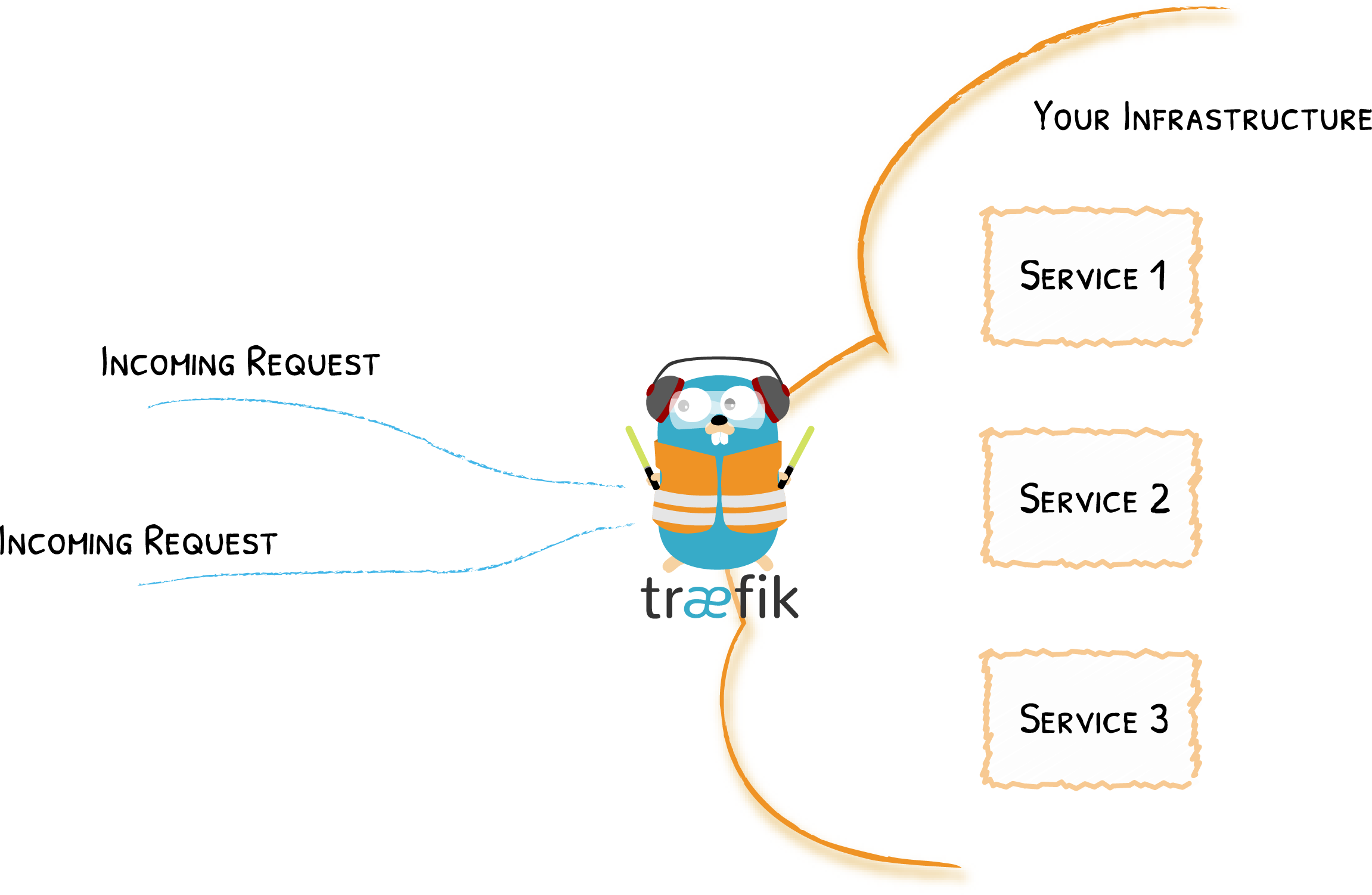
Dynamically Discovers Services
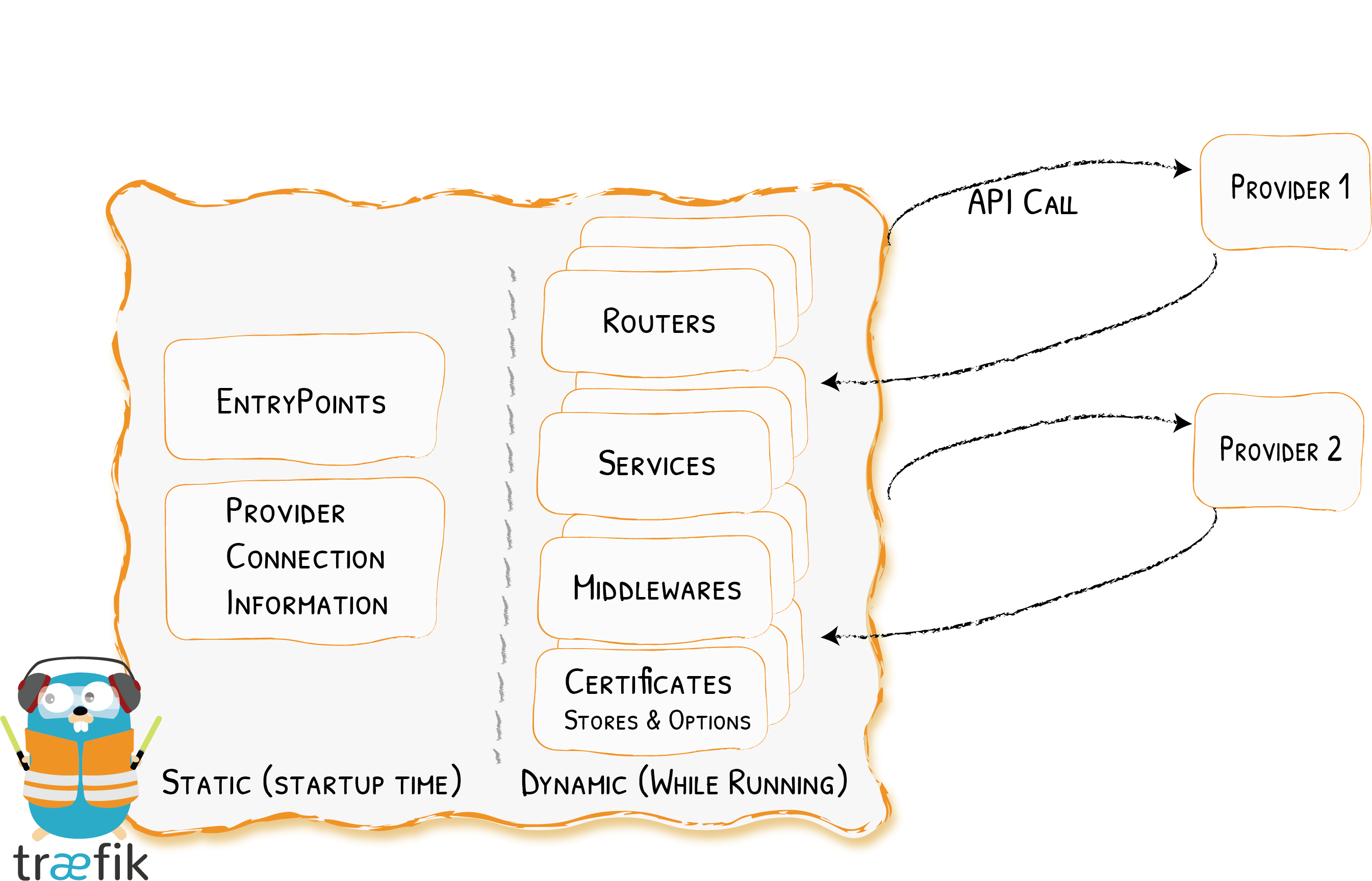
Architecture (v2.0) at a Glance
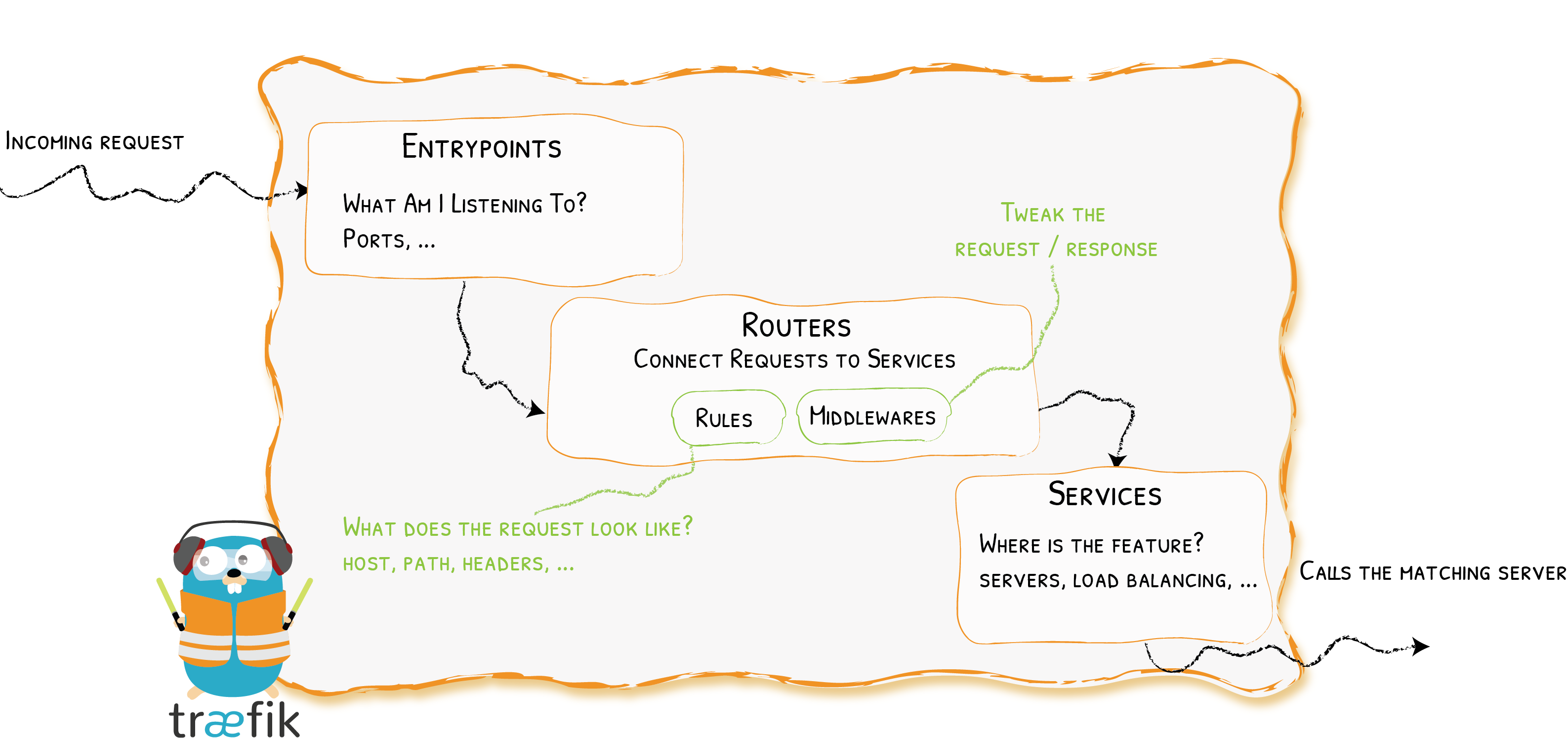
Entrypoints
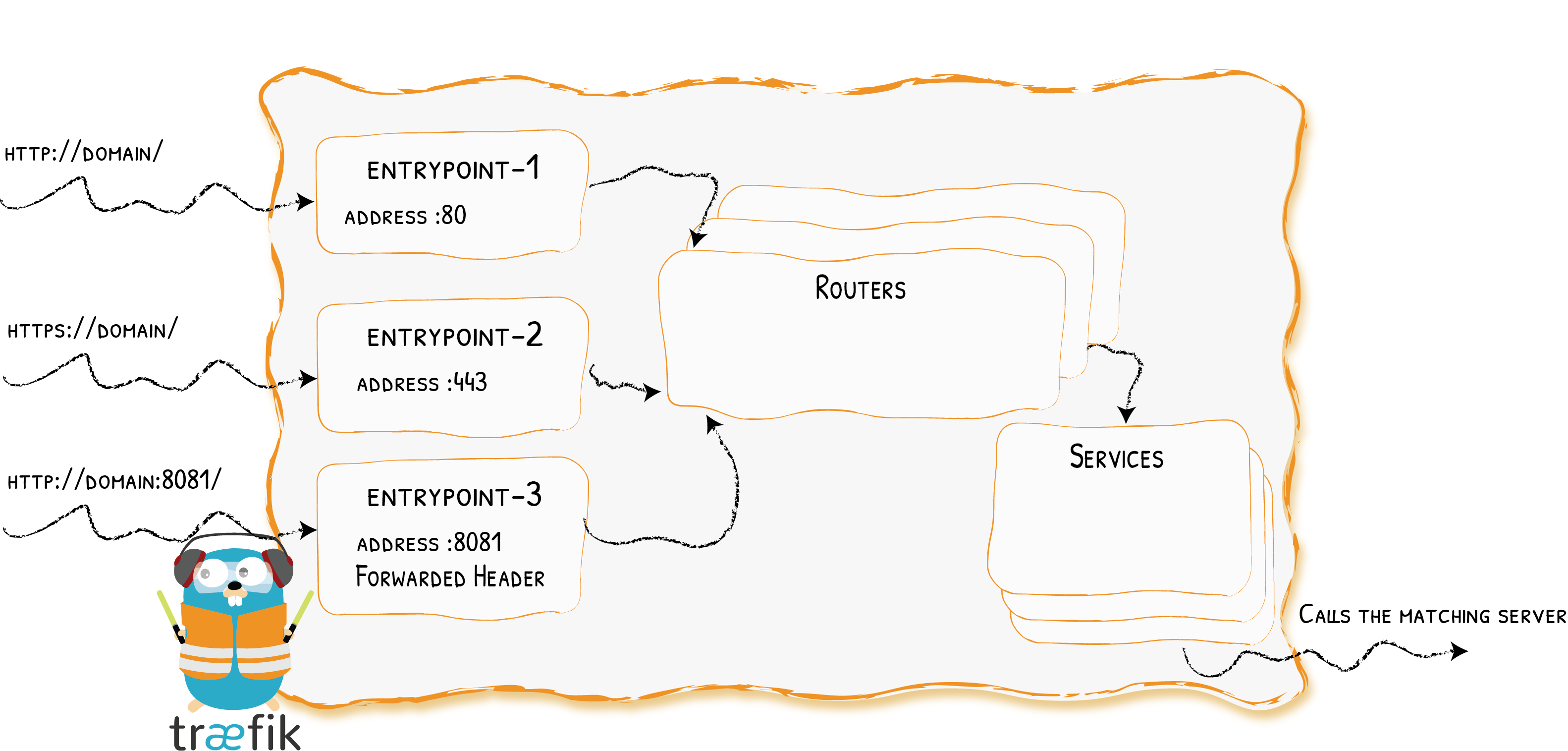
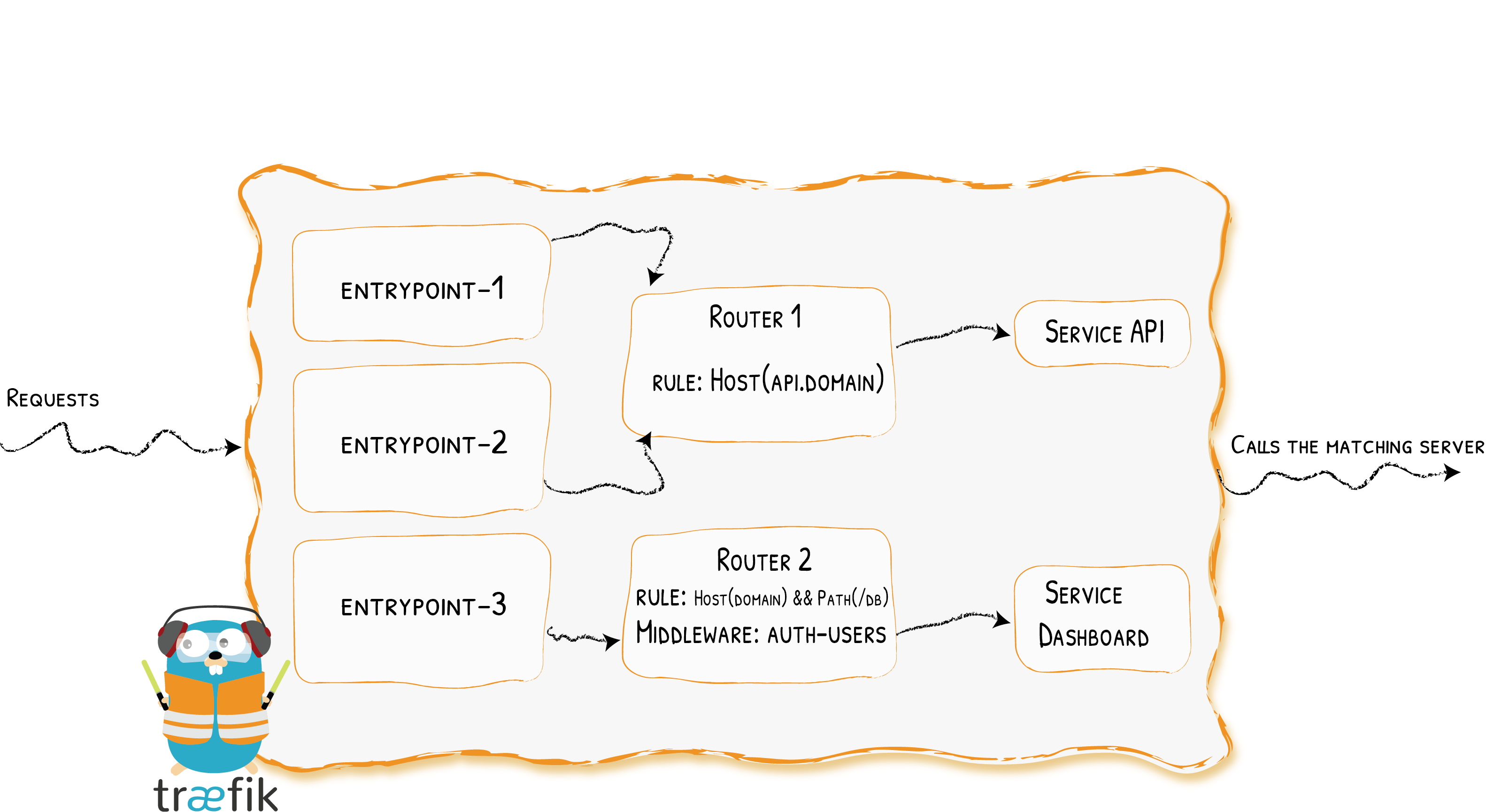
Routers
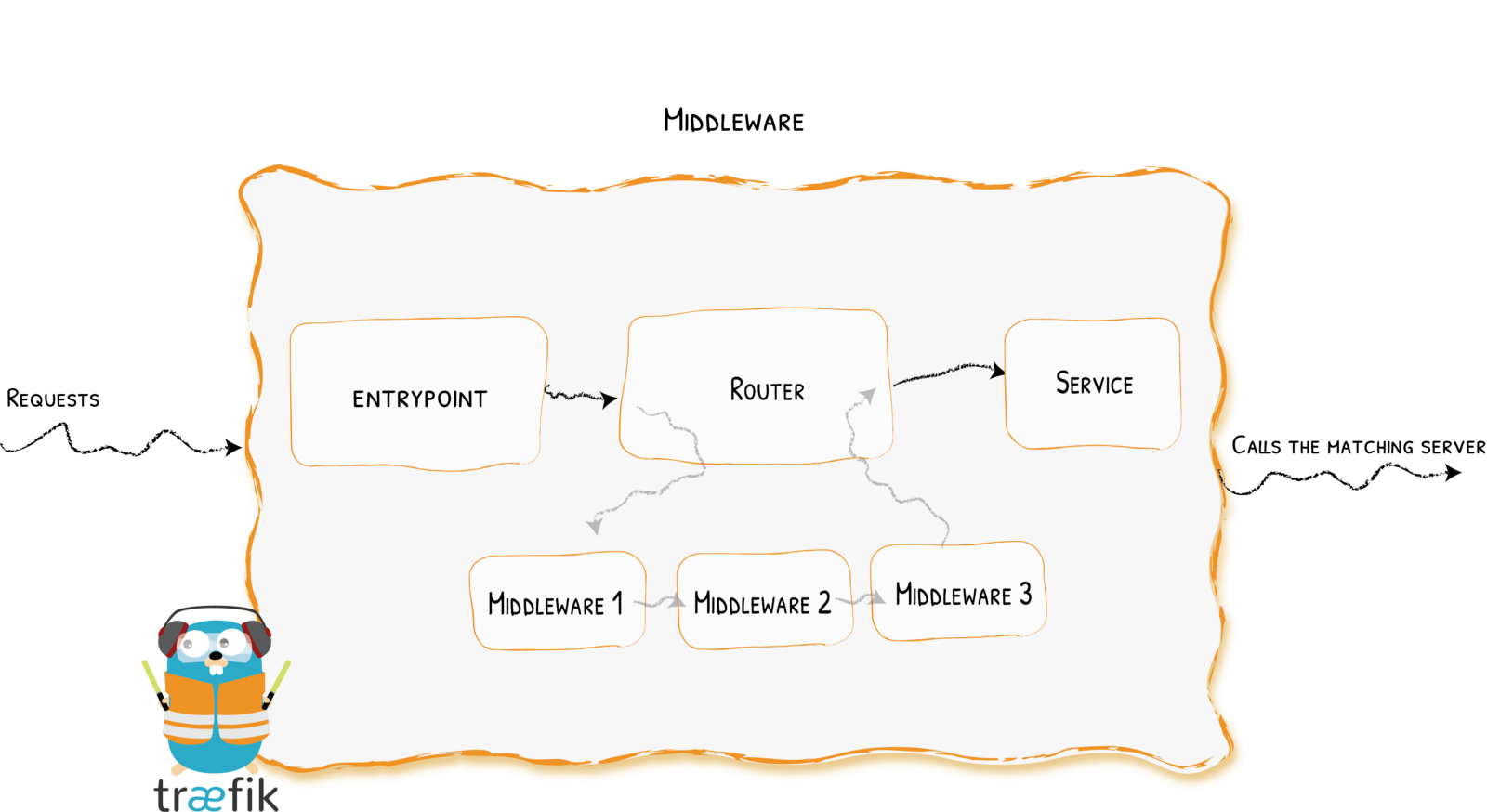
Middlewares
Services
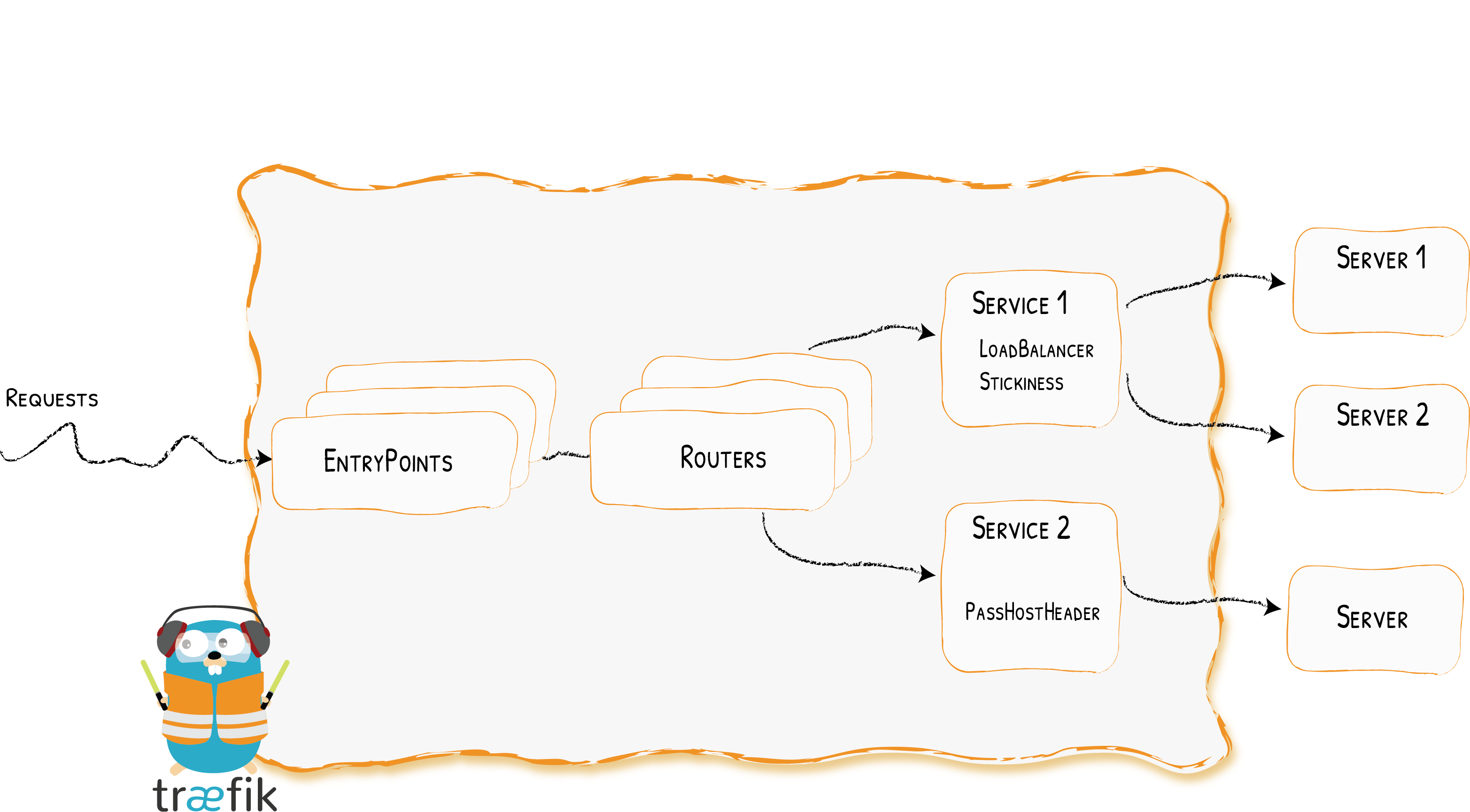
Architecture (again) at a Glance

Static & Dynamic Configuration
Show Me the Configuration!
Traefik with 🐳
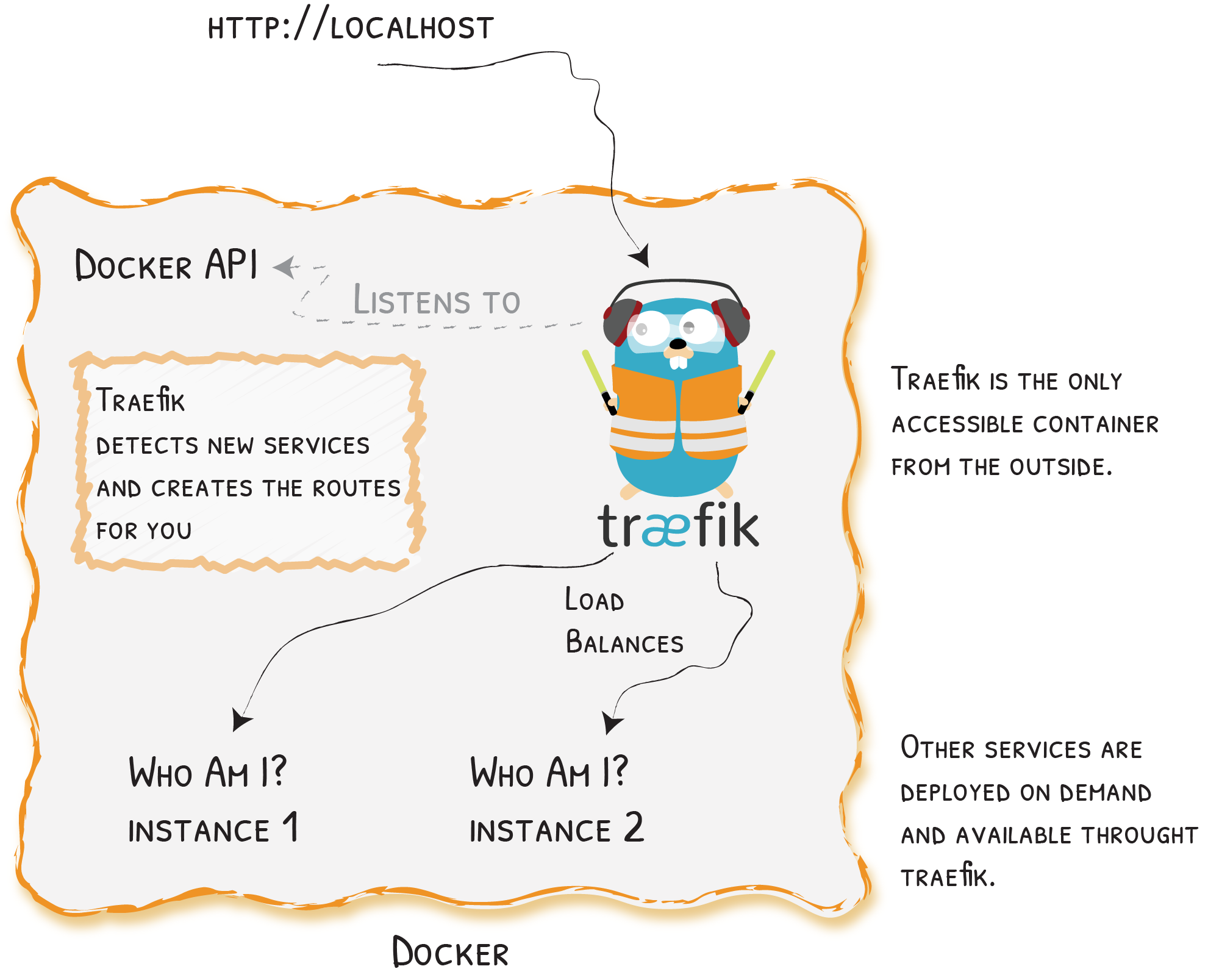
Example With 🐳
version: '3'
services:
reverse-proxy:
image: traefik:v2.0
command: --providers.docker.endpoint="tcp://proxy-docker.svc.local:2376"
ports:
- "80:80"
corporate-webapp:
image: company/corporate-webapp:1.2.3
labels:
- "traefik.http.routers.webapp.rule=Host(`company.com`)"
admin-webapp:
image: company/admin-webapp:15.2.2
labels:
- "traefik.http.routers.admin-webapp.rule=Host(`company.com`) && PathPrefix(`/admin`)"
- "traefik.http.routers.admin-webapp.service=admin-svc"
- "traefik.http.services.admin-svc.LoadBalancer.server.Port=9999"Traefik With ⎈
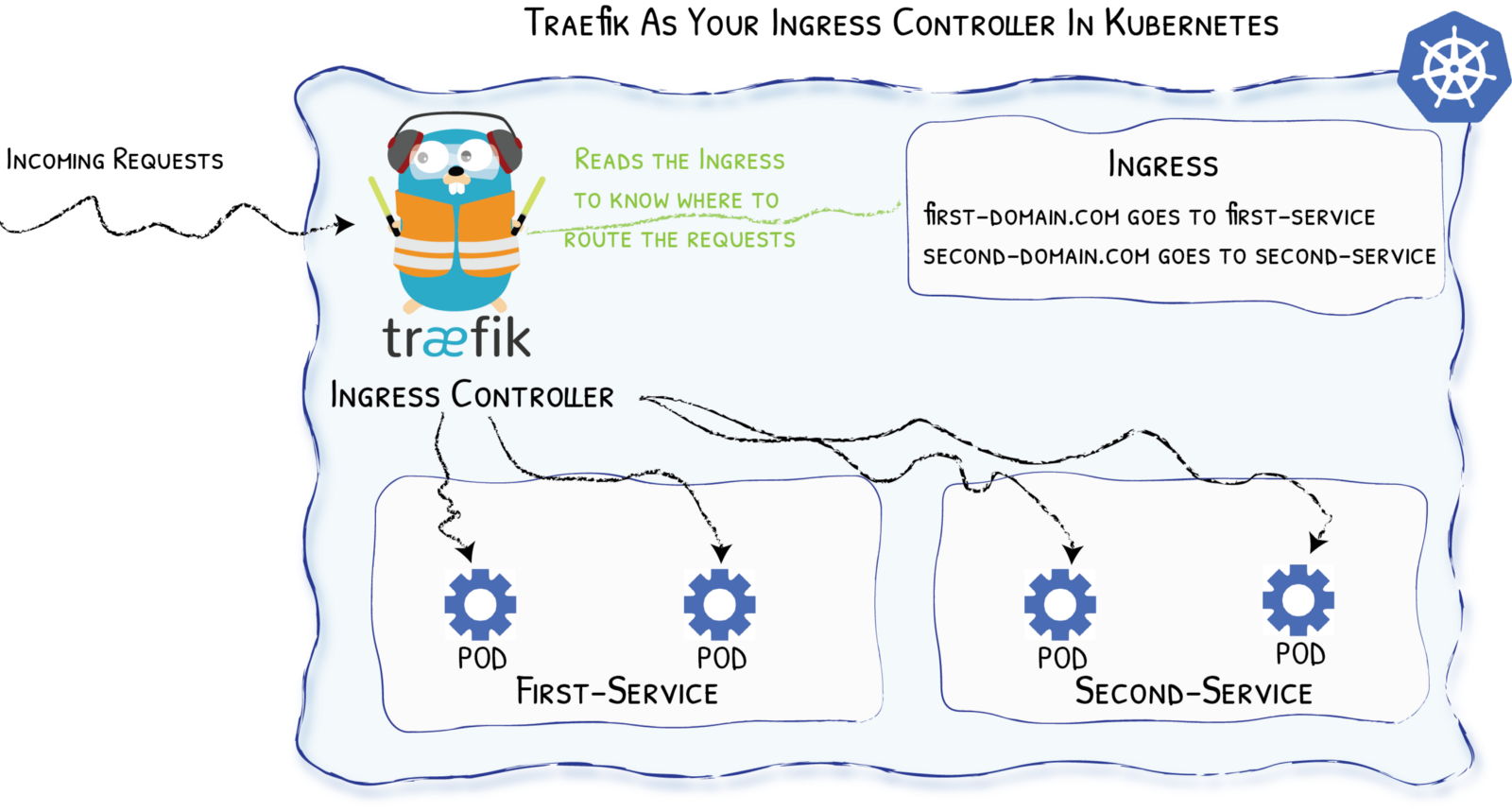
Ingress Example with ⎈
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: corporate-webapp
annotations:
kubernetes.io/ingress.class: 'traefik'
spec:
rules:
- host: localhost
http:
paths:
- backend:
serviceName: corporate-webapp
servicePort: 80But…
⎈ CRD - Custom Resources Definition
# File "webapp.yaml"
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: simpleingressroute
spec:
entryPoints:
- web
routes:
- match: Host(`localhost`) && PathPrefix(`/whoami`)
kind: Rule
services:
- name: webapp
port: 80$ kubectl apply -f webapp.yaml
$ kubectl get ingressroute⎈ & TCP (with CRD)
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRouteTCP
metadata:
name: ingressroutetcpmongo.crd
spec:
entryPoints:
- mongotcp
routes:
- match: HostSNI(`mongo-prod`)
services:
- name: mongo-prod
port: 27017Demo

Demo Menu
Install Traefik v2 in Kubernetes cluster
Deploy and expose an HTTP application
Deploy and expose a TCP application
Install Traefik in Kubernetes
🛠 Custom Resource Definitions
👮 Configure RBAC
To allow watching the Kubernetes API
📦 Install Traefik as a Deployment
🚪 Expose and 📣 publish Traefik with the right Service type
LoadBalancer,NodePort?
✅ Configure Traefik and its features
Example: HTTP application
📦 Install the web application as a Deployment
🚪 Expose the web application with a Service of type
ClusterIPInternal access only
📣 Publish the web application with an
IngressRoute
Example: TCP application
Example with MongoDB:
📦 Install MongoDB as a Deployment
🚪 Expose MongoDB with a Service of type
ClusterIPInternal access only
📣 Publish MongoDB with an
IngressRouteTCP
More to come
New Helm Chart for v2.0
Advanced Load-Balancing with CRDs: Canary, Mirroring, StickySession, etc.
Available today with
FileandDockerproviders
Example and Guides
UDP?
More info

We Also Missed Talking About …

Traefik also comes in Herd
As Simple As Traefik
Install it:
# Cluster Installation
traefikeectl install \
--licensekey="SuperSecretLicence" \
--dashboard \
--kubernetes # Or --swarmConfigure it:
# Routing Configuration, same as Traefik's
traefikeectl deploy \
--acme.email=ssl-admin@mycompany.org
--acme.tlsChallenge
...Free Trial
East / West Traefik
Say Hello to Maesh

What is Maesh?
Maesh is a lightweight, easy to configure, and non-invasive service mesh that allows visibility and management of the traffic flows inside any Kubernetes cluster.
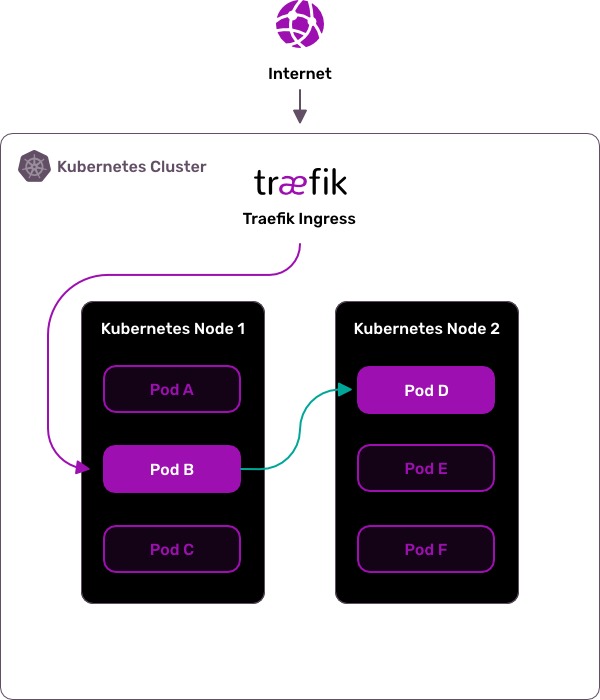
Maesh Architecture
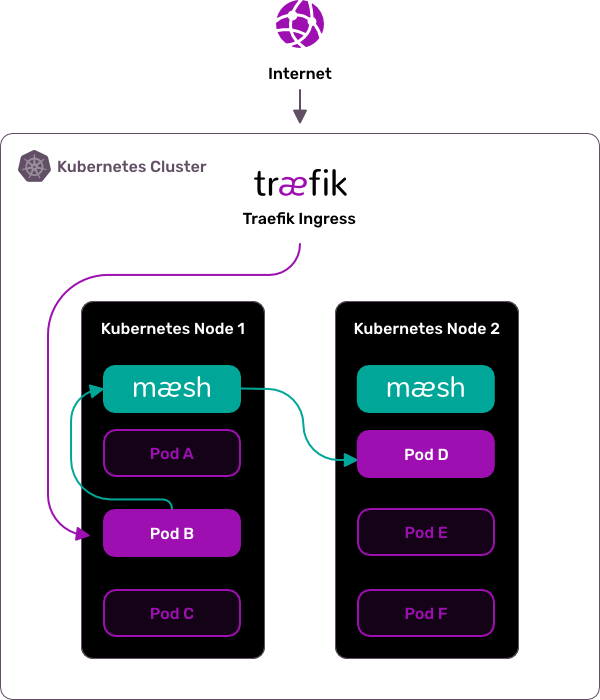
More on Maesh
Built on top of Traefik,
SMI (Service Mesh Interface specification) compliant,
Opt-in by default.
Show Me The Code!
Install Maesh (Helm Chart):
helm repo add maesh https://containous.github.io/maesh/charts helm repo update helm install --name=maesh --namespace=maesh maesh/maesh --values=./maesh/values.yamlDeploy Applications:
kubectl apply -f apps/0-namespace.yaml kubectl apply -f apps/1-svc-accounts.yaml kubectl apply -f apps/2-apps-client.yaml kubectl apply -f apps/3-apps-servers.yaml kubectl apply -f apps/4-ingressroutes.yamlDeploy SMI Objects to allow traffic in the mesh:
kubectl apply -f apps/5-smi-http-route-groups.yaml kubectl apply -f apps/6-smi-traffic-targets.yaml
A Closer Look to SMI Objects
apiVersion: specs.smi-spec.io/v1alpha1
kind: HTTPRouteGroup
metadata:
name: app-routes
namespace: apps
matches:
- name: all
pathRegex: "/"
methods: ["*"]
---
apiVersion: access.smi-spec.io/v1alpha1
kind: TrafficTarget
metadata:
name: client-apps
namespace: apps
destination:
kind: ServiceAccount
name: apps-server
namespace: apps
specs:
- kind: HTTPRouteGroup
name: app-routes
matches:
- all
sources:
- kind: ServiceAccount
name: apps-client
namespace: appsThat’s All Folks!
We have
stickers!
We are hiring!

docker run -it containous/jobsThank you!
